macOS
Syslog
syslog. Since macOS Sierra (10.12, 2016) Apple has redesigned its log system. Unix logs were replaced (syslog, for example). By the way, syslog was replaced as well on iOS (see here). Some still exist: daily.out, cups, install.log. 🛑 More about logs for iOS and macOS here.
🛑 More about fervents here.
New unified log path in 2 directories:
/var/db/diagnistics/var/db/uuidtext
According to Apple docs, NSLog now doesn’t write to syslog, therefore I didn’t find a syslog.sock or syslog file itself.
Important
The unified logging system is available in iOS 10. and later, macOS 10.12 and later, tvOS 10.0 and later, and watchOS 3.0 and later. This system supersedes the Apple System Logger (ASL) and Syslog APIs.
That’s why now with newer devices you can’t view logs with
socat - UNIX-CONNECT:/var/run/lockdown/syslog.sock
# gives an error
socat[2520] E connect(5, LEN=31 AF=1 "/var/run/lockdown/syslog.sock", 31): No such file or directory
ondeviceconsole tool won’t help either, since it uses the same socket (see main.c):
#define SOCKET_PATH "/var/run/lockdown/syslog.sock"
There is a socket file syslog (checked by trying to cp it), but using the above techniques with it didn’t work.
NSlog
With newer versions of iOS the Oslog API is used. To see the logs, use oslog utility from Cydia repository or Passionfruit multitool. Can pipe to grep to filter output.
Fsevents
Directory events only 10.5-10.6. File events since 10.7. Each record is assigned a name which is constucted the following way: hex(last_event_id + 1). Lots of zeroes appended at the beginning of the file name. Example: 000000000112f2d8.
⚠️ Records are stored alphabetically, not chronologically!!! By alphabetically I mean sorted by file/dir full path.
/.fseventsd # root of the system partition
Like $UsnJrnl for Windows. Contains lots of logs gzip-compressed archive files. Magic number: 1SLD or 2SLD in an uncompressed file marks a page.
Log entries contain file ids which is useful for sequencing files and events. Since there are dozens of entries, it’s better to filter them. “Renamed” can mean the file was moved on the same volume.
Like $UsnJrnl. ❗️It keeps track of file ids, which is useful for sequencing events. Can be found /.fseventsd. Lot’s of gzip archives.
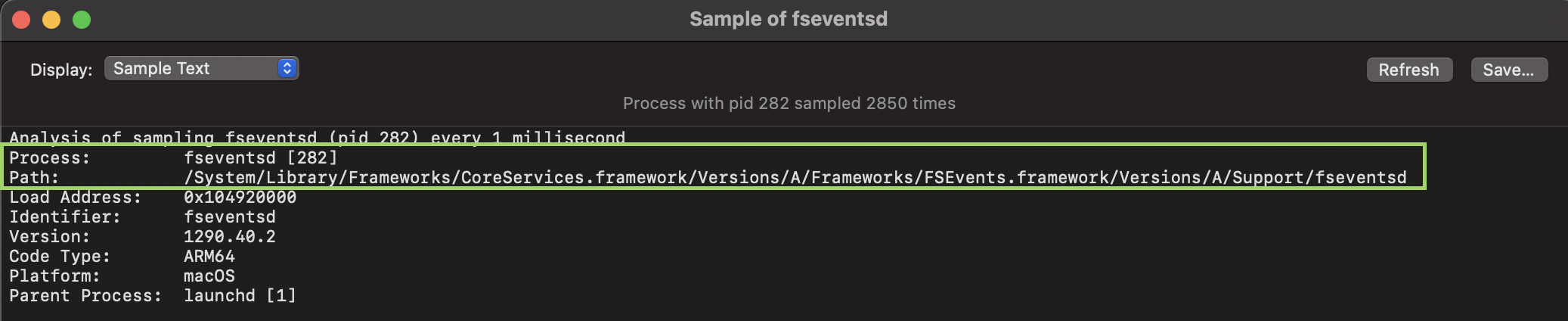
🧪 However, I couldn’t find it on my M1 (macOS Big Sur, 11.2.3). The daemon was running (checked with Activity Monitor). Grabbing the processes path on disk (search for
fseventsd, double-click, chooseSampleand get the path from the result)👌 I have found it here:
./System/Volumes/Data/.fseventsd. On iOS -/private/var/.fseventsd, for System:/.fseventsdand Developer Patch at/DeveloperPatch/.fseventsd.
python FSEParser_V3.3.py -s -t folder /.fseventsd -o /Users/sentinel/Desktop/FSEvents_Out
Keywords: Mount/Volume, Safari/Chrome (web search), Renamed/.trash (trash).
Lot’s of information, so, think well whether to process it or not, since it’ll take time.
⚠️ If you insert a FAT-formatted thumb drive into a macOS machine, it will create fervents.
Mount, Unmount, Volume. See here to know more about this artefact. Directory events only 10.5-10.6. File events since 10.7. Each record is assigned a name which is constucted the following way: hex(last_event_id + 1). Lots of zeroes appended at the beginning of the file name. Example: 000000000112f2d8. Can be found in either of these locations:
/.fseventsd./System/Volumes/Data/.fseventsd- On iOS -
/private/var/.fseventsd, for System:/.fseventsdand Developer Patch at/DeveloperPatch/.fseventsd.
python FSEParser_V3.3.py -s -t folder /.fseventsd -o /Users/sentinel/Desktop/FSEvents_Out . More about FSEvents might be seen here [10]. Thanks to Nicole Ibrahim from OSDFCon, we have this filetype reverse engineered and documented. At least, v1.
😭 Getting an error when trying to run
FSEventsParseron a M1. No excpetion when running it on an Intel machine though. 😊 ✅ My solution was to run a windows version on a VM. Worked fine.
Mount activity: DMGs, External devices or Shared network drives.
SELECT
*, _ROWID_ "NAVICAT_ROWID"
FROM
"fsevents"
WHERE
"mask" LIKE '%mount%'
Internet activity (websites visited)
SELECT
*, _ROWID_ "NAVICAT_ROWID"
FROM
"fsevents"
WHERE
"filename" LIKE
'Users/%/Library/Caches/Metadata/Safari/History/%'
OR "filename" LIKE 'Users/%/Library/Application
Support/Google/Chrome/Default/Local Storage/%'
User folders activity
SELECT
*, _ROWID_ "NAVICAT_ROWID"
FROM
"fsevents"
WHERE
"filename" LIKE 'Users/%/Documents/%’
OR "filename" LIKE 'Users/%/Downloads/%’
OR "filename" LIKE 'Users/%/Desktop/%'
FSEventsParser. More about FSEvents might be seen here [10]. Thanks to Nicole Ibrahim from OSDFCon, we have this filetype reverse engineered and documented. At least, v1.
😭 Getting an error when trying to run
FSEventsParseron a M1. No excpetion when running it on an Intel machine though. 😊 ✅ My solution was to run a windows version on a VM. Worked fine. ✍🏻 Another solution is to use mac_apt.py
mac_apt.py. Requires python to be installed. Consists of: extract_apfs_fs, ios_apt, mac_apt_artifact_only, mac_apt_mounted_sys_data and mac_apt.
Usage example:
python mac_apt_artifact_only.py SCREENTIME -i "/Users/username/Documents/RMAdminStore-Local.sqlite" -o "/Users/username/Documents/"
Querying Interesting Data
SELECT
*, _ROWID_ "NAVICAT_ROWID"
FROM
"fsevents"
WHERE
"filename" LIKE 'Users/%/.Trash/%'
010 Editor Template
I’m writing a template for parsing these files. However, the v2 seems to be a little different from the v1, which was described in the presentation mentioned above. Below is the structure of a file header + single page for v1.
🔬 v2 might need more research from my part.
//------------------------------------------------
//--- 010 Editor v11.0.1 Binary Template
//
// File:
// Authors:
// Version:
// Purpose:
// Category:
// File Mask:
// ID Bytes:
// History:
//------------------------------------------------
SetForeColor( cRed );
char header[4];
SetForeColor( cNone );
int unknown;
SetForeColor( cYellow );
int pagesize;
SetForeColor( cPurple );
string full_path1;
uint64 event_id;
int reason_flags;
The structure is however quite trivial. Following the header of 4 bytes and 4 bytes of some undocumented mysterious value, there are 4 bytes defining page size, the full path of the file and the event id of the event.
❓ May be it’s better to write a script for 010 Editor?
Turning Off Logging
From Apple’s official documentation:
In some cases, the contents of a volume are sufficiently secret that it is not appropriate to log them. To disable logging on a per-volume basis (for creating a backup volume, for example), you must do the following:
- Create a
.fseventsddirectory at the top level of the volume.- Create an empty
no_logfile in that directory.So if your volume is mounted at
/Volumes/MyDisk, you would create an empty file called/Volumes/MyDisk/.fseventsd/no_log.
Problems
Problem #1. When the USB drive or another external media is not safely removed (by ejecting it properly, not just viciously unplugging it like a sword 🗡 from the corps by some primeval man from the Middle Ages), the fsevents will have no time to write to the file. If the device was unplugged too soon, this may also result in lost events (even if the sword analogy could not be applied here). If the FS on the device is incompatible, the same result you’ll get.
Problem #2. When several operations were performed on the same file or directory, there is only one record for that in the logs. I presume, as long as these events are sufficiently sparsed in memory, the get to different buffers, thus to different files and this would be the only way to observe changes.
🧪 How long does it take for a fsevent buffer in memory to fill up?
Problem #3. They can be turned off. But that would require sufficient knowledge of logging system on macOS. Most users of macOS are not forensics experts, I presume. Not even hackers. Though there are many of them… However, even those are not experts in macOS.
Problem #4. Fsevents logs do not keep timestamps. See the rightmost column. How’s that likely, that all of these events have the EXACT same timestamp? Not very. That’s source_modified_time. To overcome this limitation Ibrahim [1] recommends using temporal data from the names of logs.
🧪 Not quite sure what he meant by that… .
🧪 I presume, that’s the date and time when the log files were created. Or is this the date and time when
FSEventsParserwas performing its duties?
🗑 Trash activity
SELECT
*, _ROWID_ "NAVICAT_ROWID"
FROM
"fsevents"
WHERE
"filename" LIKE 'Users/%/.Trash/%'
Unified logs
/private/var/db/diagnostics
Linux
/var/log 🐧
/etc/rsyslog.conf - see the log owners, what specific logs are logging and where the additional configurations are stored.
cd rsyslog.d && less 50-default.conf - to see additional configurations: what specific logs are logging, how they are called and where to find them.
sudo less syslog - most of the system logs.
auth.log - authorisation messages
kern.log - kernel messages
To configure what is being logged, how and when, go to /etc/audit. apt-cache search auditd (if it’s not installed). nano audit.rules files to open. Config example:
-w /etc/shadowto keep track of the users added/deleted/modified.w- watch file:-p- watch for permission;wa- look for writes;-k <name>- give the name of this log entries.
a always,exit- look for actions:- generate alerts
always; - look for specific syscall
-S clock_settime; -k <name- give the name of this log entries, for example,timechange.
- generate alerts
To start auditing, run the daemon: service auditd start. The results are stored in /etc/audit.log.
Sysmon
eBPF -> sysinternalsEBPF (based on libbpf). eBPF allows programs to run in a sandbox within OS. Microsoft has customised it and sysinternalsEBPF was created to monitor security events on Linux.
https://github.com/Sysinternals/SysmonForLinux, eForensics Magazine, Linux Forensics and Security, Enhance Visibility And detection On Linux With Sysmon, by Sergio Figueiredo.
References
Expand…
https://xakep.ru/2021/09/16/linux-audit/ [1] OSDFCon, Introduction to FSEvents
[2] Preventing File System Event Storage, official Apple docs


