Nearly all IP (intellectual property) are recreated by a competitor. Investigate the development machine
Potential data exfiltration.
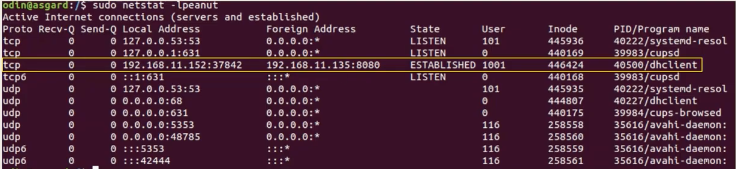
netstat -lpeanutshows that there are two dhcp clients running, one using unusual port and user:
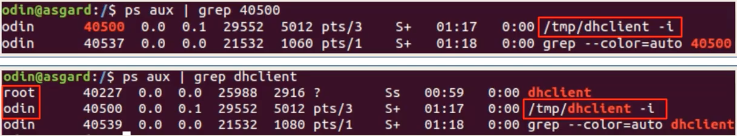
ps aux | grep 40500orps aux | grep dhclientshows the running processes and sometimes commands used to run them. This suspicious client was run from/tmpfolder:
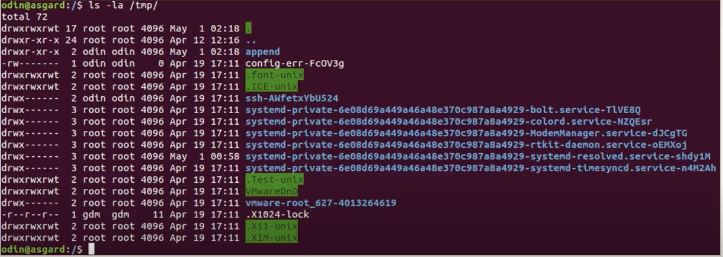
ls -la /tmp/to see the file that was launched. But nothing there. Seems that the file was deleted after being launched:
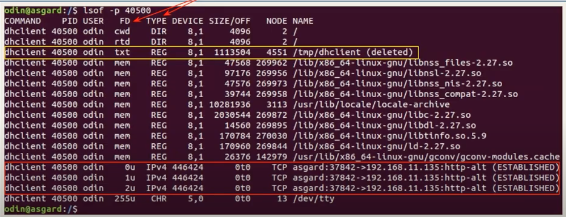
lsof -p 40500to see the files the were opened by the prog with certain PID. Shows that dhclient was indeed deleted and the socket files still open (red):
❗ In Linux a file can be deleted and still be run.
/procfsis like a snapshot of RAM. Linux maps its memory to a temp virtual file system. Explore as it’s mapped onto the disk.cd /proc/40500/andls. Seeexesymlink in red. Runls -lto see where the symlink points to and it points to the deleted suspicious file 🦹♂️. But despite this, one can still get the file from memory.
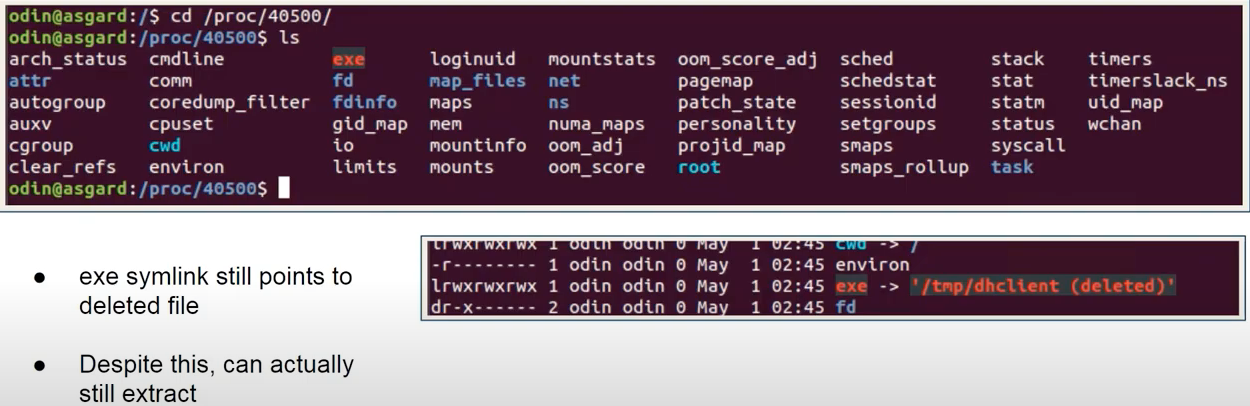
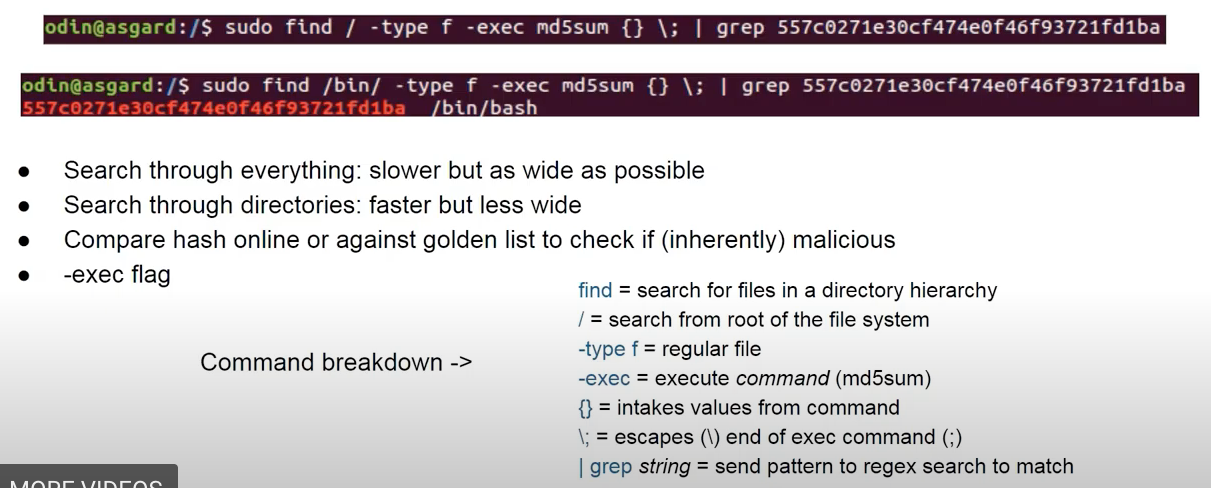
cp /proc/40500/exe /tmp/copyandcat /proc/40500/exe > /tmp/reassembled. Compare hashesmd5sumandsha1sum.- Find these hashes in other directories (in case it was copied) and on other machines
sudo find / -type f -exec md5sum {} \; | grep <hash_from_step_5>orsudo find /bin/ -type f -exec md5sum {} \; | grep <hash>:
References
[1] Magnet webinar on Linux Forensics


