- Running
netstat, see the weird python script with established connection to some remote host:
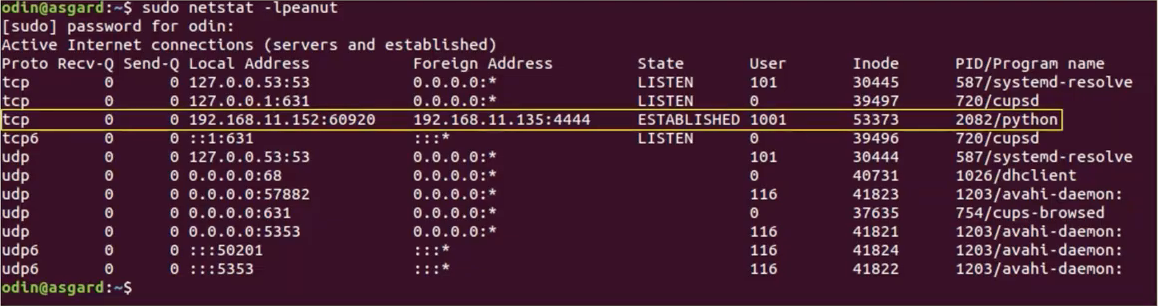
- Grab the executable:
lsof -p 2082andps aux grep 2082.
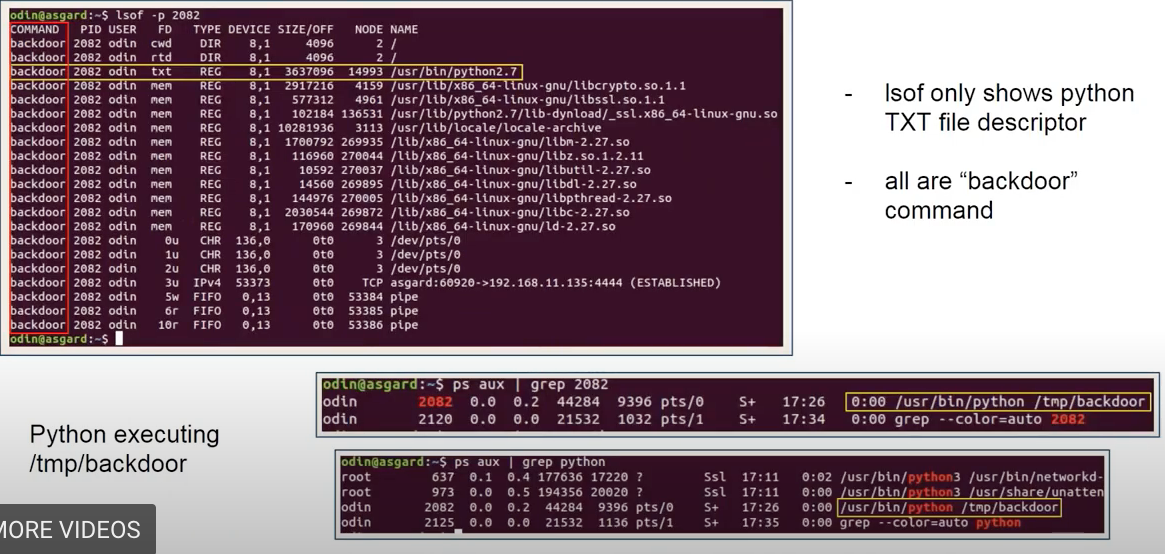
- Let’s see the
/tmp/folder forbackdoorexecutable - Check
/proc/2082andls
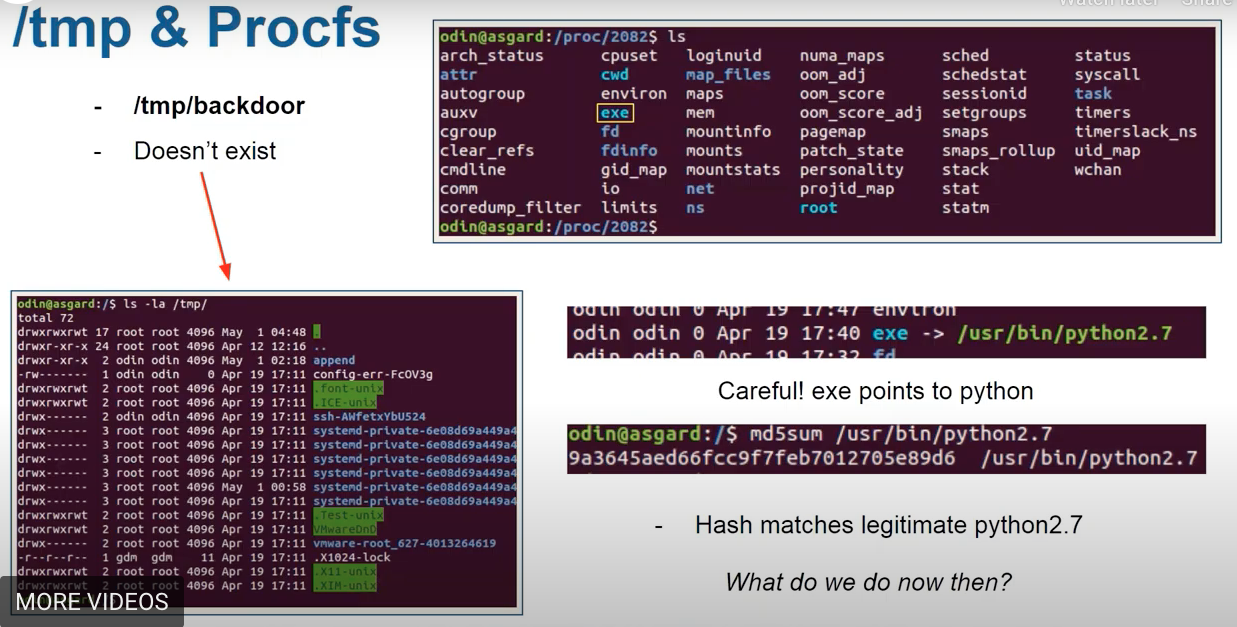
- Since the executable is a legitimate python, need to explore further. In
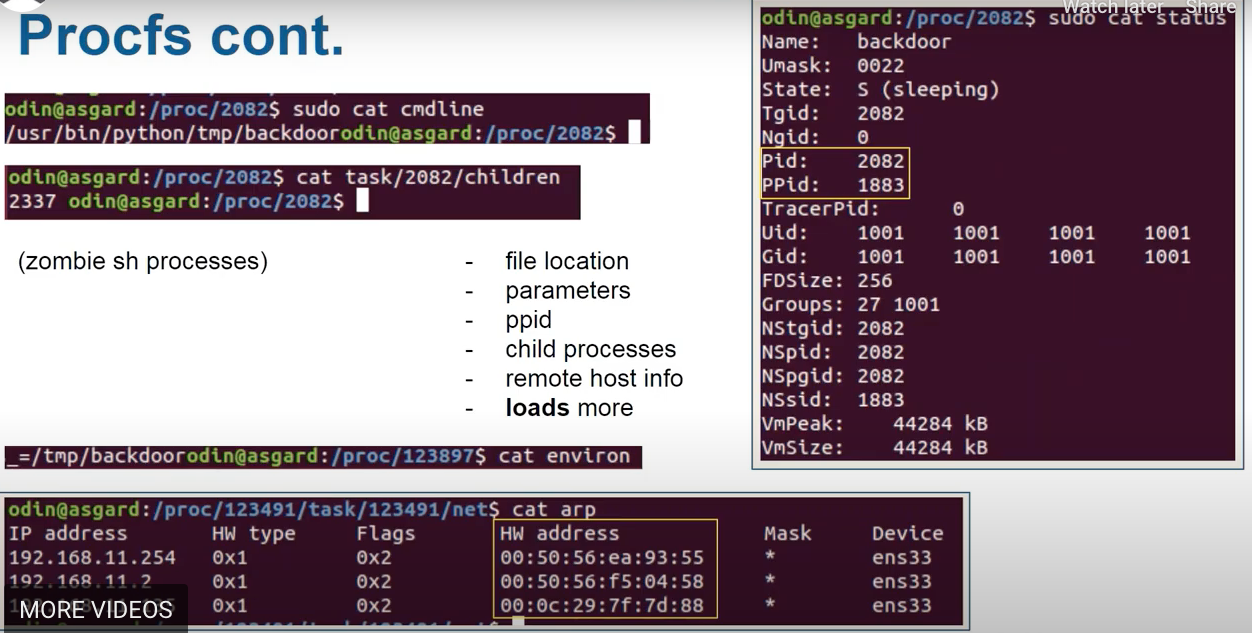
/proc/2082runsudo cat cmdlineshows the comand used to launch,cat task/2082/childrenshows children PID.sudo cat statusshows general information.cat environshows … .cat arpshows MAC addresses of the machines connected:
- Get the backdoor file: file recovery or memory forensics. Sometimes
/procfscan manage.
References
[1] Magnet webinar on Linux Forensics


