Case Overview
Arya Stark gets an email presumably from Direwolf with an attachment. It looks suspicious and she forwards it to the Security.
Identify possible threats. Identify attack vectors: Website hosting malicious content waiting for a vulnerable browser. This can be countered with: Qradar, McAfee ePolicy Orchestrator, Next generation firewall.
In Qradar we have several alerts: Malicious URL detected, three possible DDoS and OAS denied access and continued preceded by file infected.
IBM X-Force Exchange, checking for the URL, why is it malicious.
There were three alerts in Qradar:
- Malicious URL detected:
weberdut.co. Check the domain. It might have been malicious in the past, but now it might be clean. If it is still detected as malicious - create a ticket. - Potential DDoS attack detected containing DNS Server Error:
192.168.1.13,192.168.1.11. Qradar and firewall detected lots of session open/closed events. Going to events revealed that these were requests local-to-local which is typically a normal traffic for a developer, for example. Closed as a non-issue. - Potential DDoS attack detected containing RT_FLOW_SESSION_CLOSED:
192.168.1.12. Closed as a non-issue for the same reasons listed above. - OAS denied access and continued preceded by file infected. Qradar shows the system and the file name:
eicar.com. This file has a unique signature used to test antivirus software. So this might be a probe.
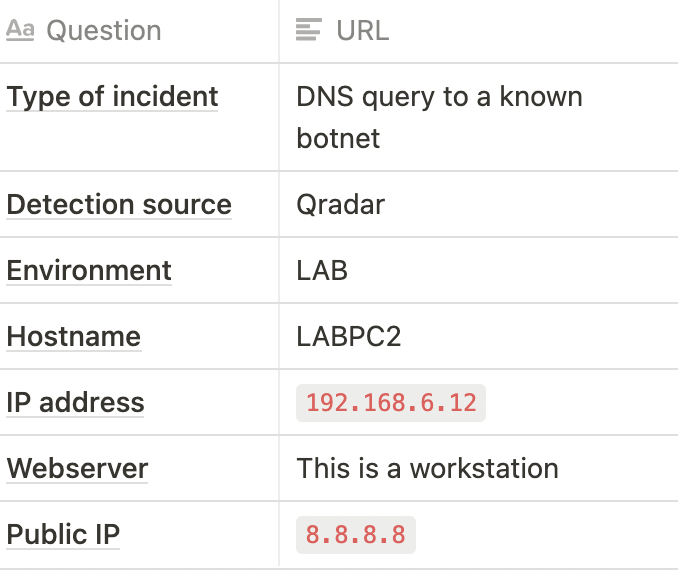
Ticket example:
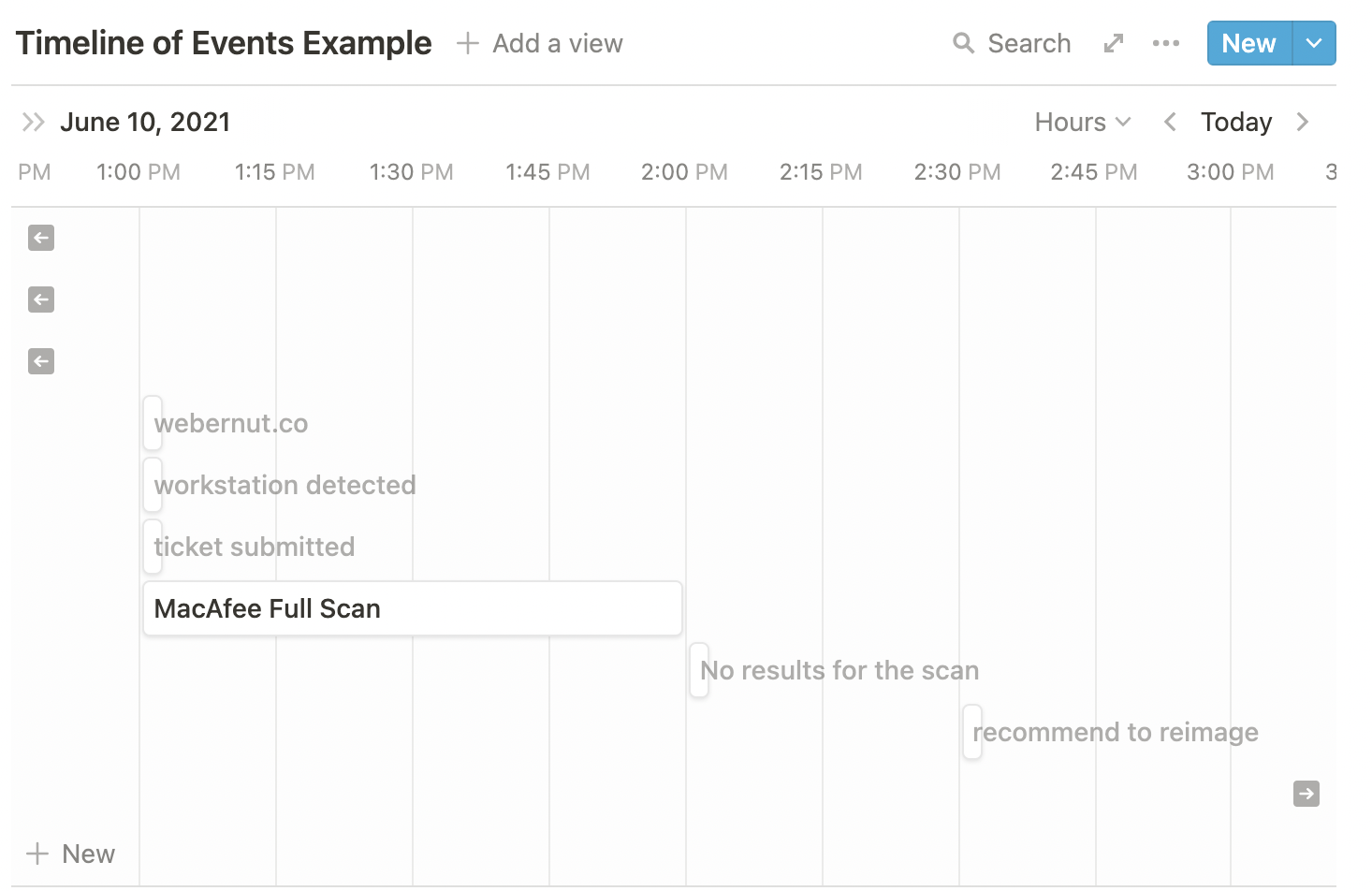
Timeline example:
References
[1] IBM course


