There are lot’s of evidence of installation and execution. Based on this data one can prove that the user knew about it or not. Below are the main evidence, tools for analysis and .
It’s not always about malware. Sometimes it’s just about user activity.
Evidence of Execution
\Windows\Prefetch
\Windows\appcompat\Programs\RecentFileCache.bcf
\Windows\appcompat\Programs\Amcache.hve
\Windows\appcompat\Programs\Amcache.hve.LOG
Dr Watson
Drwtsn32.log, traps a crashing program. Can create a file named User.dmp. 100% prove that the program was executed.
Installed programs and applications
Key 🔑: Microsoft\Windows\CurrentVersion\Uninstall. There can be some data for programs that do not exist on the system anymore. The last write time is when the application was installed.
Key 🔑 Microsoft\Windows\CurrentVersion\Appx\AppxAllUserStore for installed Microsoft applications. Defines between those that were installed for a specific user or system-wide.
Key 🔑: Wiw6432Node (SYSTEM hive root node) - those that run a 32-bit mode. Separate sub-keys for different versions of a program.
Key 🔑: Classes\Installer\Products - installed using Miscrosoft installer (those with msi extension).
Prefetch
Expand …
Prefetch is for efficiency of starting processes and their resources (movies for media players, spreadsheets for Excel for example). Improves startup time of applications. Each prefetch file name follows the pattern: <EXENAME>-<PATHHASHED+CMDARGS>.pf.
ℹ️ Information Contained
- Filename
- Creation time
- Modified time
- File Size
- Process EXE
- Process Path
- Run Counter
- Last Run Time
- Missing Process + libraries and resources for each process.
- Forensics value - tracks the execution of programs. Central repository of what was run on the system. File size can be used to search for the same process with a different name on a different machine.
⏰ Timestamps
Filesystem Timestamps. The first time the executable is run, a pf file is created. The last time it was run - a pf’s file Modified date and time. However, consider a scenario when a program was run long time in the past, wasn’t run for a while after that. Its pf file was overwritten (prefetch keeps 1024 entries). Some time after that the executable is run again and the pf file is created again. The FS timestamps will show that the file was first executed recently when it’s not quite that straithforward.
🔎 Structure and Analysis
If collecting prefetch on a live system, run volatile collection tools before that and collect pf files to avoid overwriting oldest prefetch with prefetch for live response tools (or disable prefetch before collection).
Path to files: C:\Windows\Prefetch. All prefetch have a signature at offset 4th byte. MAM - compressed and SCCA - plain text.
| OS | Signature1 (version) | signature2 (type) |
|---|---|---|
| WinXP & 2003 | 0x00000011 or 17 | SCCA |
| Vista | 0x00000023 or 23 | SCCA |
| W8 | 0x0000001a or 26 | SCCA |
| W10 | MAM | 0x04 |
| W10 | 0x0000001e or 30 | SCCA |
Prefetch can be disabled in registry C:\Windows\System32\config\SYSTEM, key 🔑: HKLM\SYSTEM\CurrentControlSet\Control\SessionManager\MemoryManagement\PrefetchParameters\Enable Prefetcher:
| key | meaning |
|---|---|
0 |
disabled |
1 |
enabled for apps only |
2 |
enabled for boot only |
3 |
boot and app enabled (default) |
You can check it with rip.exe:
rip.exe -r SYSTEM -p prefetch # to show whether prefetch is enabled
🤨 Caveats
On servers is usually turned off. And starting with Win10 - compressed. For systems with solid state drives it’s also disabled. With Win8 - additional run times recorded. Also, there is latency issue - some apps are not closed upon clicking X, but remain running in background. Hence, the last time run might be different.
If the app was deleted and then reinstalled? What the firtst run time will be?
What if I rename an executable?
If the exe is substitued?
If the same exe was run from different locations - different .pf files. If the application was deleted, the info remains in prefetch.
Write a sctipt to determine deleted files
🛠 Tools
WinPrefetchView. To view pretech files (decompressed as well) in GUI.
Fred - Forensic Registry Editor. To view exported hives.
FTK Imager Lite. Fairly heavy footprint - 15-16Mb.
CDQR. This tool focuses on the pf intself rather than on a data it contains. It’s useful for making timelines.
RegRipper (GUI and CUI).
rip.exe -r SYSTEM -p prefetch # to show whether prefetch is enabled
Prefetch parser. More info than with WinPrefetchView
prefetch.py -c -d -e
prefetch.py -c -d > pf.csv
prefetch.py -f <file_to_parse> > pf.txt
Columns: last executed, MFT sequence number, MFT record number, executable name, run counter,
PECmd. Eric Zimmerman’s tool.
PECmd.exe -f <pffile>.pf
PECmd.exe -d "Prefetch folder" --csv "outoutdir" --csvf "outputfile"
AmCache
Expand …
Path to file 🛣️: C:\Windows\AppCompat\Programs.
Since Windows 8. Stored information about program execution, including those, that were run from a USB drive.
ℹ️ Information Contained
- install date and time
- name
- version
- path to exe/dll
- source info
- path to uninstall
- publisher name
- volume GUIDs
- container ID of the device from which the program was run.
DeviceCensus - some information about the physical machine itself. For example, for my Parallels VM there was also a VM subkey that contained some value VMId.
File. Full path to the executable.
⚠️ Not present on my Windows 10 (Parallels VM).
InventoryApplication. Consists of folders/subkeys named by the program id. Each folder will contain the following important information: OSVersionAtInstallTime, InstallDateMsi, InstallDate, InstallDateArpLastModified, InstallDateFromLinkFile, Name, Publisher, RegistryKeyPath (may show user SID), Source, UninstallString, ProgramID (consistent accross systems).
⚠️ On my Parallels Windows 10/11 machine I noticed that here not only Windows, but also Mac executables are listed even though I have specifically set in preferences that I am not sharing Mac folders or disks with the VM.
InventoryApplicationFile. Contains a fileid which is actually a SHA-1 hash, padded with 4 leading zeros and full path to the executable. Use a list of known good or VirusTotal.
InventoryDeviceContainer. Contains ModelName and FriendlyName. When devices get connected, they might install some software to be able to work correctly.
InventoryDevicePnp. Contains ContainerID, DriverID, Description, Manufacturer and Model.
Programs. Where this program is located within the FS and the source (for example, AddRemoveProgram). And also information path to the uninstaller in registry.
⏰ Timestamps
🛠 Tools
AmCacheParser.exe + Timeline Explorer.
AmcacheParser.exe -f <path_to_AmCache.hve> -i on --csv <export_to_folder_no_quotes> --csvf <desired_filename>
What are unassociated files? Those that are not associated with a known source. Good starting point when looking for bad files.
⚠️ In my case on a macOS with Parallels and Windows 10 installed, this evidence also contained mac executables.
AppCompatCache aka ShimCache
Key 🔑: CurrentControlSet\Control\Session Manager\AppCompatCache\AppCompatCache.
🛠: ShimCacheParser.py (requires Python2), AppCompatCacheParser
Originally was used to identify compatibility issues between 32 and 64 bit progs. Track the file path, size, last modified time ⏰. Only logs specific file extensions. It might not be a reliable evidnce that the program was executed or even installation, but if the program was installed and deleted - it won’t be deleted from here. ShimCache is another name for this artifact. Uses file system timestamps.
If the executable is modified or renamed, new entry will be created, but modified date and time will be the same for both files even after these actions take place. $UsnJrnl is another place to make sure that is what had happened. $Logfile.
⚠️ Written at shutdown!
⚠️ Doesn’t track the file execution for Win7+ systems.
BAM
Key 🔑: ControlSet001\Services\BAM.
⚠️ Windows 10 only!
Background Activity Monitor. Organaized by user SID. Windows apps’ names are not parsed very well here. Gives last executed time ⏰ , 64-bit little-endian (first 8 bytes of the value). It does prove program execution and it ties it to the specific user. May use the same technique for core processes analysis and identifying rogue processes like in RAM.
MUICache
Key 🔑: Local Settings\Software\Microsoft\Windows\Shell\MuiCache.
Installed and executed applications for that particular user. But no timestamps for this acts, only last write data and time for the key in registry.
ComDlg32
Key 🔑: NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32.
CIDSizeMRU- Tracks applications globally. MRU start at zero. Timestamp for the most recent item only. FirstFolder -tracks the install locations of applications, full path to the app, but no exact file name. OpenSavePidMRU - tracks files that were saved with Save As dialog, or opened with Open dialog. Tracks autocomplete terms. LastVisitedPidMRU - tracks the specific executable used by an application to open the files documented in the OpenSaveMRU key. Also tracks the directory for the last application accessed for each file in OpenSavePidMRU, tracks the location the file existed.
Jump List Data
Key 🔑: NTUSER.DAT\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\JumplistData.
Shows applications accessed.
Recent Apps
Key 🔑: NTUSER.DAT\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\RecentApps.
Similar to User Assist. Also shows files and applications that were used through this application. This key consists of sub-keys that are marked with application’s GUID. Some of them will have Recent Items sub-key (10 max), each has Last Write Time (Windows 64-bit, little-endian).
⚠️ Not all Win10 machines will have this key.
Key 🔑: Software\Microsoft\Windows\Current Version\Explorer\RunMRU.
A list of the programs that have been run from the Run command is shown. Each time you use a command that has already been stored, it moves to the top of the list.
User assist
Key 🔑: NTUSER.DAT\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Assist.
List of progs and applets that can be quicly started from the Start menu for usability, the most often used items. Shows a focus count for each entry. It means, how many time was the window switched to (that doesn’t include the time when the program is first run). Shows the last time that the program was executed, focus time, run count.
At the start of each entry between {} is the code for a location within file system. Registry Explorer will substitute these automatically, since these GUIDs are predefined.
This what a full filled User Assist key looks like. {CEBFF5CD-ACE2-4F4F-9178-9926F41749EA} is for programs that were lauched using their image files directly. {F4E57C4B-2036-45F0-A9AB-443BCFE33D9F} is for those, started with a shortcut.
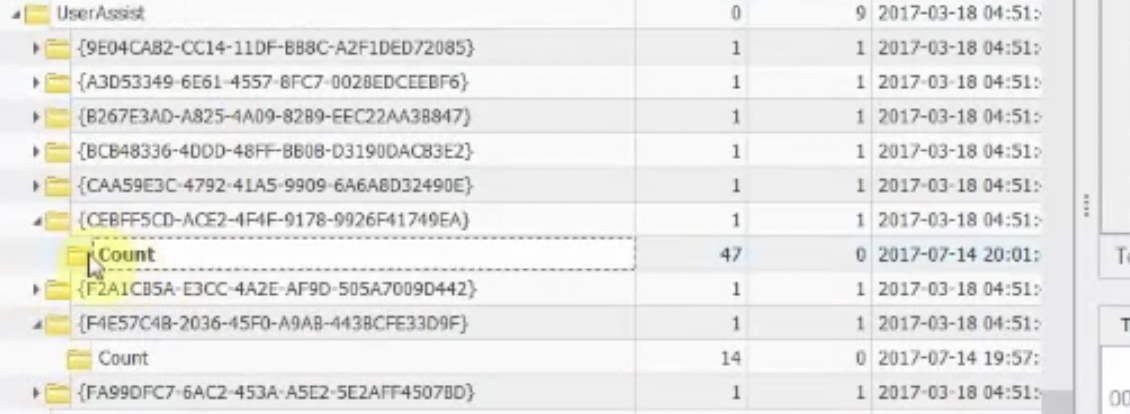
The structure is quite simple:
- At
0x04offset starts the number of executions (4 bytes). - At
0xCoffset starts the focus time (4 bytes) - At
0x3Coffset starts the Last Execution time (8 bytes), which is a Win64-bit little-endian value (for Decode 🛠).
⚠️ 🔎 I could not find this key on my Win10 VM.
⚠️ When the program was started via
lnkfile, the focus count will be0.
Uninstalled applications
Key 🔑: Microsoft\Windows\CurrentVersion\Uninstall


