Open connections.
Ports idetify services (usually, but not always).
- System ports are forensically important
0-1023. - User ports
1024-49151 - Private
49152-last
Cheatsheets for known ports here.
Private IP addresses:
- 10.0.0.0 - 10.55.55.55
- 17x.0.0.0
- 19x.0.0.0
Make a list of notable ports and IP addresses.
netstat -boan statistics and current tcp connections along with the exe, listening port and PID. For Mac OS netstat there is no -o switch, so I’ve used netstat -ban. 👣 Check for Windows Security Event Log 5156 is triggered when a network connection is allowed. 4688 - new process starting. 5158 -> 5031 binding started and terminated by fw.
Filter out internal addresses (they are not interesting initially). Check the remote connections. Check executables that launched these connections, also look for port-services mismatch or unusual ports or services. ☝️ malware section as well.
Windows
5158 5154 ->
5158 -> 5031 binding started and terminated by fw.
PID, Application field (path to the executable and exe name), Inbound/Outboun, sport/dport, addresses (src and dst), protocol field.
If you don’t see some event ids that you are supposed to, then try turning on all auditin policy using secpol.msc or going to Start -> Windows Administrative Tools -> Local Security Policy. In the opened window then go to Local Policies and choose Audit Policy. Either turn on each of them or turn on the ones that you think are responsible I was able to star capturing event 5156. I was using Vbox with Windows Server 2019 installed and the machine promoted to DC (Active Directory Feauture installed).
Example of suspicious case: java listening on port 53 which is normally used by DNS service. FF using 3389 port (which is for remote connections). 44999 (used for private internal connections) some strange executable.
Filter out internal addresses (they are not interesting initially). Check the remote connections. Check executables that launched these connections, also look for port-services mismatch or unusual ports or services.
📝 Make a list of processes and connections of several clean systems for “known-good” reference.
Windows Security Event Log 5156 is triggered when a network connection is allowed. 4688 - new process starting.
write-EventLog -eventID 5156 -EntryType FailureAudit -message "hello"
>Log Application
>Source Application
auditpol /set /subcategory:”Filtering Platform Connection” /success:disable /failure:enable

External IPs reputations. 🛠 hostintel. For running the tool, you’ll also need to create a file with a list of IPs. I’ve created a file i.txt in the hostintel directory and so my command was:
python hostintel.py config.conf i.txt
Filter the record to indentify external IP addresses with which the PC is commincating. Then check external IPs reputations for suspicious using, for example, hostintel.
To use hostintel, install it following the instructions on GitHub. Then install geoip2 using pip install "geoip2==3.0.0" . I got an error that geoip.database was not installed when I installed it with pip install geoip2 or from GitHub. This module is for working with GeoIP databases.
To actually use these databases (one is included with the tool, but it mught get outdated), signup here and download GeoLite2 City from here. This is an archive, unpack it and put the *.mmb file in hostintel/data folder (replace). These dbs are used by other tools as well, so you might want to keep it elsewhere and change its path in config.
Also, about the config. Edit this config - hostintel/sampleconfig.conf. By default, only GeoLite2 City is used, but you can add your free public API keys from different threat intelligence resources like VirusTotal, Censys, OTX, Passive Total or/and Shodan. You might want to rename it more appropriately, like config.conf or aliens-are-among-us.conf 👽. But keep in mind the name of the config, whatever it is, to run the tool.
Frequency Analysis. How frequently is the host connecting to another machine? For how long? May be it is something legitimate. But if it’s recent or/and not regular - might be an indicator.
Unusual. Unusual application names, paths, typos or pokerhand ports (44488 12345 or alike). Or may some gibberish names. Unusual protocols - 1 (ICMP) 6 (TCP) 70 (UDP). Look for the ports outside of these three.
Malware
https://malware-traffic-analysis.net
DNS
Windows DNS Cache
in research.
DNS names
Check IP reputation: www.reverse.it, www.urlvoid.com.
Encrypted Traffic
TLS
- The plaintext content can be retreived from RAM.
- MiM
UNIX
lsof -i :443will show you all connections associated with port 443, commonly used for TLS communication. Sheward, Mike. Hands-on Incident Response and Digital Forensics (p. 163). BCS Learning & Development Limited. Kindle Edition.
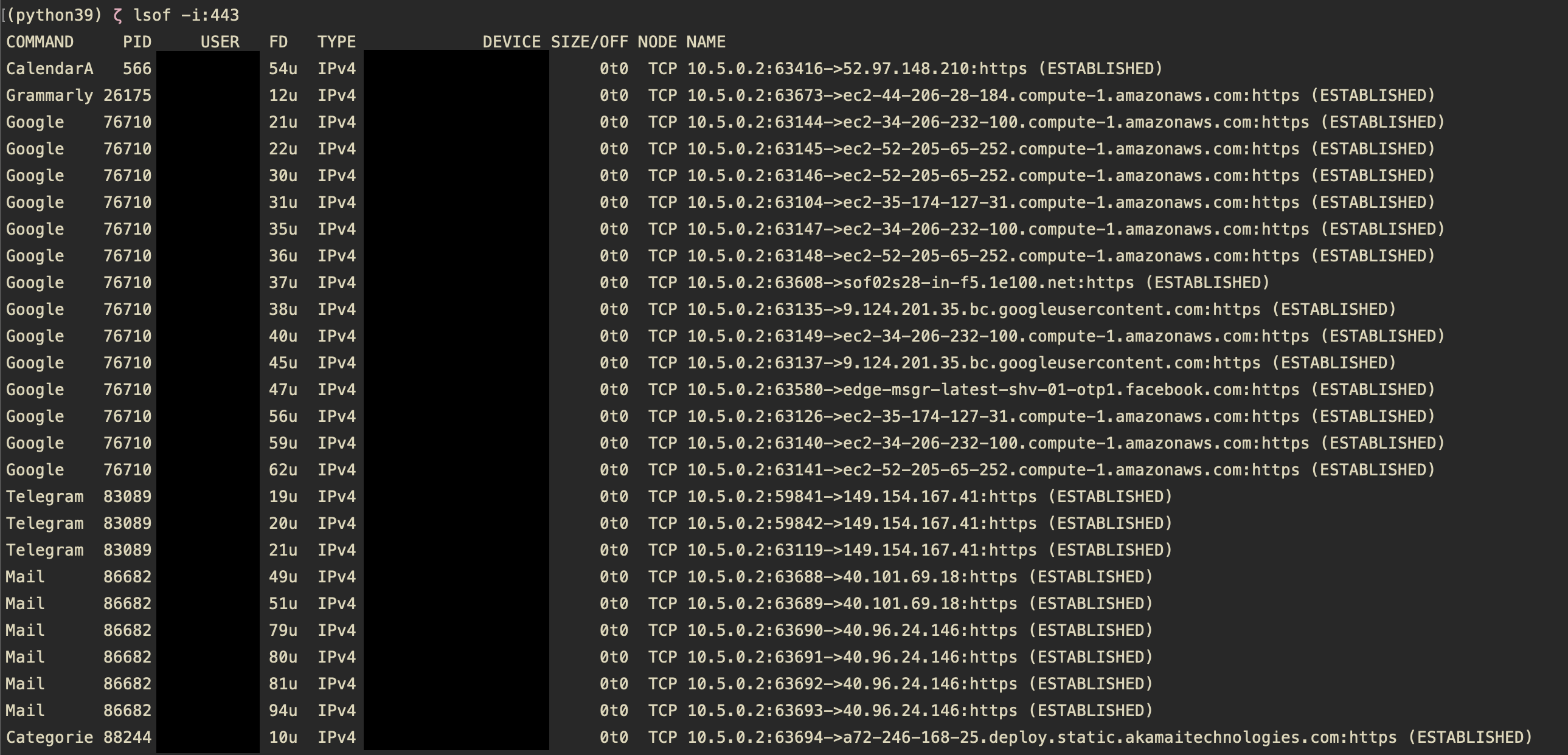 The first column will give a hint about what the application responsible for this connection is. To get the full path to the app executable, use
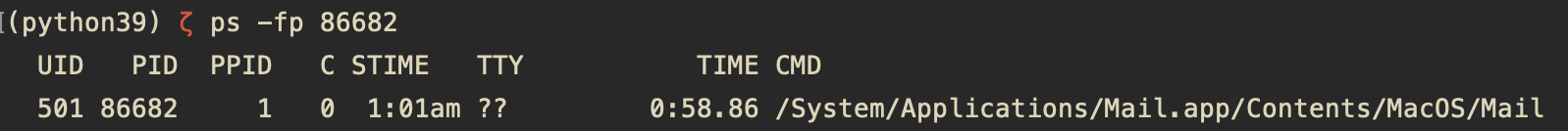
The first column will give a hint about what the application responsible for this connection is. To get the full path to the app executable, use ps -fp <PID> command:
Windows
Run netstat -a -n -o to get the list of connections and then use tasklist with the PID of interest to see information about the process.
SSH
🛠 Tools
ExtraHop or ntop (see Chapter 1) provides insight into the amount of data being transferred and to where even when that data is encrypted.
Wireshark Filters
http.request - show only HTTP request. Useful to get rid of all ARP and TCP handshake garbage.
ip.src == 192.168.22.94 and udp.port == 67 - show the DHCP requests for this machine. Can show the computer name.
Todo
💡 For each common nmap scan get the footrprint
💡 For each common DoS attack get the footprint
💡 Footprint for sqlmap
💡Footprint for common vulnerability scanners
Network Analysis with Dshell
Please refer to the Toolkit sections, Forensics Lab Setup for installation steps.
decode -p rtp -i wlan0 # see all auido and video traffic
decode -d dns 2022-11-07-part-1-of-2-Emotet-infection.pcap # view DNS request from the pcap
Not sure how this is better than Wireshark + filtering.
📘 BTFM 📕 RTFM
nslookup
> set type=ns
> bakerst221b.com
> set type=mx
> bakerst221b.com
References
[1]NSLOKUP, DIG and HOST utilities usage


