zip
brew install john
brew install hashcat
brew install maczip # to create test 7z on macOS
./7z2john /path/to/zip/file.7z > /path/to/output/file.hash
hashcat -h | grep -i zip
11600 | 7-Zip | Archive
17220 | PKZIP (Compressed Multi-File) | Archive
17200 | PKZIP (Compressed) | Archive
17225 | PKZIP (Mixed Multi-File) | Archive
17230 | PKZIP (Mixed Multi-File Checksum-Only) | Archive
17210 | PKZIP (Uncompressed) | Archive
20500 | PKZIP Master Key | Archive
20510 | PKZIP Master Key (6 byte optimization) | Archive
23001 | SecureZIP AES-128 | Archive
23002 | SecureZIP AES-192 | Archive
23003 | SecureZIP AES-256 | Archive
13600 | WinZip | Archive
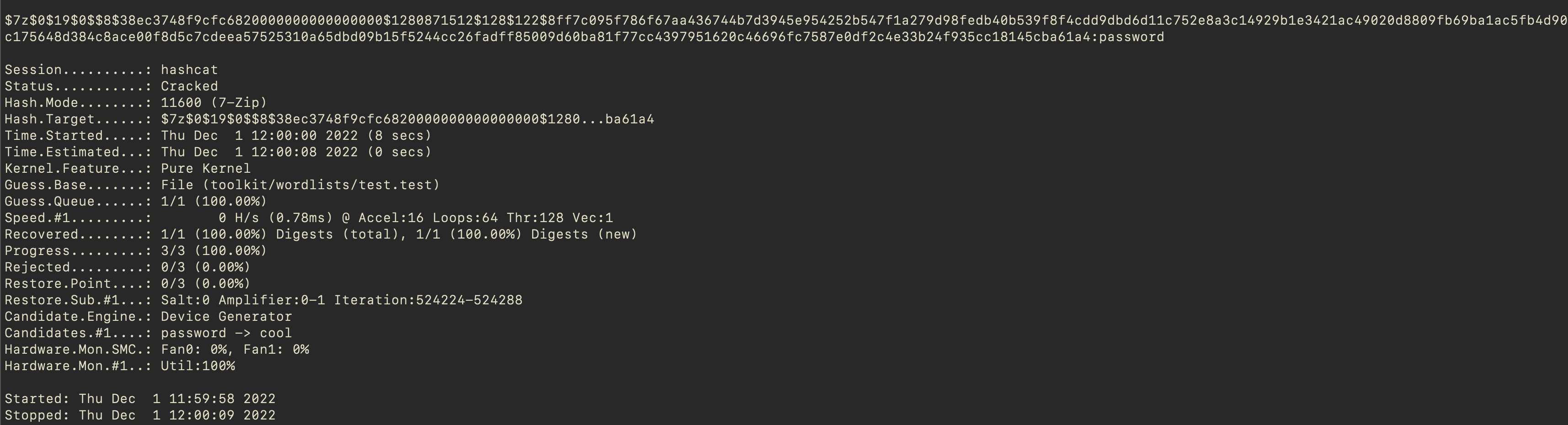
hashcat -m 11600 hash.hash toolkit/wordlists/rockyou.txt
And the result is the following. For rockyou.txt file the estimated time was about 16-18 hours. So, for the testing purposes I created a simple wordlist with just 3 words.
🛠 Tools
Installation steps and troubleshooting are listed in the Toolkit section (Forensic lab setup) of this website.
Wordlists
https://github.com/openethereum/wordlist/blob/master/res/wordlist.txt https://github.com/brannondorsey/naive-hashcat/releases/download/data/rockyou.txt


