There are two broad categories of Windows core processes. Processes that initialize system environment and those that initialize the user environment. Whatever is the category, you need to know them well in order to detect abnormal things.
Boot
BIOS, POST, Boo Loader (NLTDR), Kernl (NTOSKERNEL), files: win.sys, HAL.DLL, system.ini, sizedit.exe, config.exe, autoexec.BAT, MISCONFIG.exe.
Main Processes
Below is the overview of the main processes in Windows. There are several core process that are important to examine since malware often drool 🤤 over them. Singleton - one instance running only. One instance lsass, services, System, winint, lsm.exe ❓. If any of these having more than 1 process should be the object of further investigation.
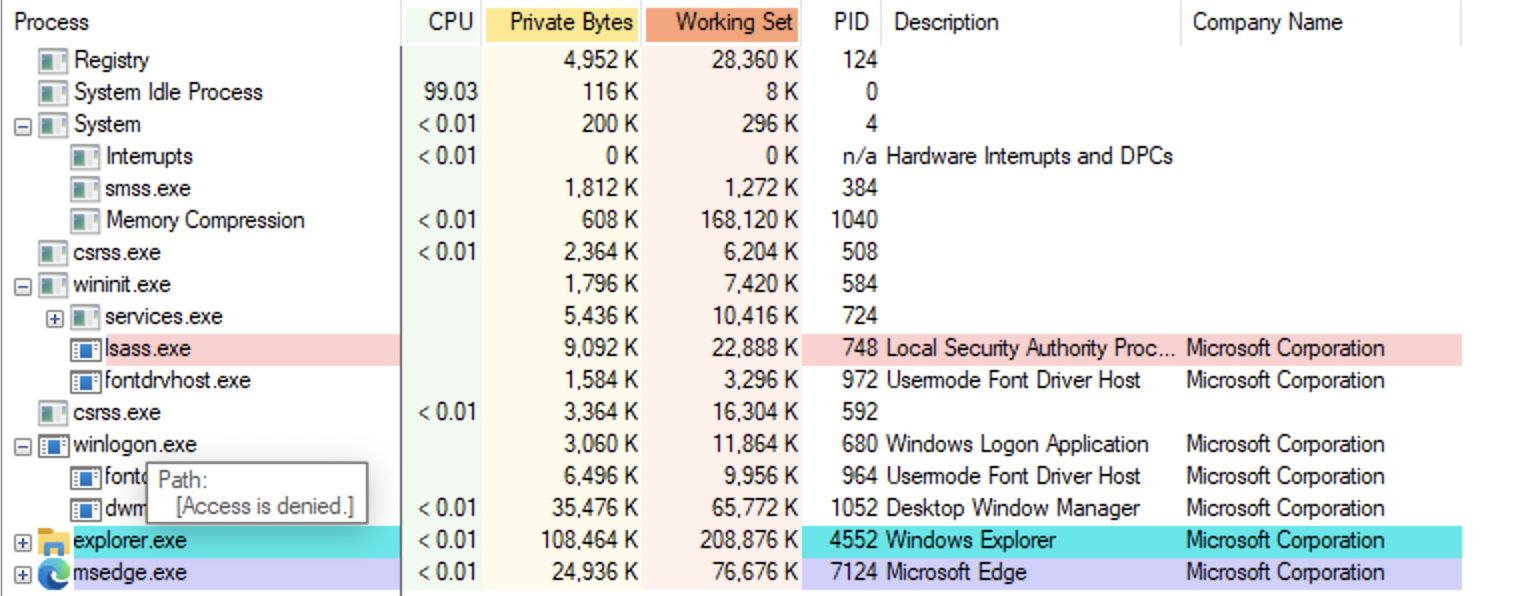
The process tree
- IDLE
- System (PID 4).
- Memory Compression
- smss.exe
- csrss
- wininit
- services
- lsass
- winlogon
- logonUI. Terminates once complete
- userinit. Terminates once complete
- explorer
IDLE or System Idle Process
Parent 🤱: None.
Children 👧 : None
Singleton ☝️:
Path to file 🛣: None
Account: Local System
Start time: Boot
The first and the most importnat process that “gives birth” to other processes - IDLE. 🔍 It doesn’t have an image file on disk, so if you see IDLE.exe, it is most likely a malware 🦠 (or you have been sophisticatedly pranked 😉). PID is usually 0.
🔎 Are
IDLEandSystem Idle Processthe same thing?🧪 If I dump a process that doesn’t have an image file, will it still have a PE header?
Runs in system memory space.
System
Parent 🤱: None.
Children 👧 : smss, Interrupts, Memory Compression
Singleton ☝️: Yes
Path to file 🛣: None
Account: Local System
Start time: Boot
Handles kernel mode system threads, different device drivers, waiting for I/O etc. PID is usually 4.
Runs in system memory space.
Memory Compression
Parent 🤱: System
Children 👧 : None
Singleton ☝️:
Path to file 🛣: None
Account: Local System
Start time: Boot
Compresses the memory of the user space. Doesn’t have an image file on disk. Not really interesting for DFIR.
smss
Parent 🤱: System
Children 👧 : None
Singleton ☝️: No
Path to file 🛣: System32
Account: Local System
Start time: Boot
Session manager process. The first user-mode process. Run from System32 directory. There are two instances:
- master instance perfroms some init stuff. Reads and writes to registry preparing the OS for use. Initializes the registry hives
- session startup instance. Creates three subsystem processes and exits: csrss.exe,
winlogon
Parent 🤱: None.
Children 👧 : None
Singleton ☝️: No
Path to file 🛣: System32
Account: Local System
Start time: varies
Another process of particilar interest is msc.
wininit
Parent 🤱: None.
Children 👧 : lsm, lsass, services
Singleton ☝️: Yes
Path to file 🛣: System32
Account: Local System
Start time: Boot
lsass
Parent 🤱: wininit
Children 👧 : None
Singleton ☝️: Yes
Path to file 🛣: System32
Account: Local System
Start time: Boot
lsass. This is the main process of Windows OS that’s responsible for authentication and authorisation. More about lsass here.
svchost
Parent 🤱: services
Children 👧 : Lots of:
Singleton ☝️: No
Path to file 🛣: System32
Account: Local System, Network Service, Local Service
Start time: Boot
🦠 This one is very ofter used by malware for disguise. It has lot’s of instances.
csrss
Parent 🤱: none
Children 👧 :
Singleton ☝️: No
Path to file 🛣: System32
Account: Local System
Start time: Boot
taskhost
Parent 🤱: services
Children 👧 : Lots of:
Singleton ☝️: No
Path to file 🛣: System32
Account: many
Start time: varies
lsaiso
Parent 🤱: winint.exe
Children 👧 : None
Singleton ☝️: Yes
Path to file 🛣: None
Account: Local System
Start time: Boot
Windows Credential Guard. Only for Windows 10 Enterprise or Windows Server 2016 and above. Also, this exe is present on a Windows 11 system, but is not running. It’s a singleton and is located on disk in System32 directory. It runs under local system account and it’s parent is winint.exe. Works in the isolated user mode, so that even the kernel doesn’t have access to it. Secure Kernel protected by Hyper-V is talking to lsaiso instead. Kernel Mode and Secure Kernel are talking using a small buffer. VSL calls. Between SK and lsaiso - sys call. VSM container: lsaiso, credentials, secure kernel, kernel mode code integrity. HVCI - Hyper-V code integrity.
mimikatz.exe
> version
privilege::debug
securlsa::logonpasswords
> misc::memssp
userinit
Parent 🤱: winlogon
Children 👧 : explore
Singleton ☝️:
Path to file 🛣:
Account:
Start time:
explorer
Parent 🤱: userinit. Since the parent terminates once it’s done everything, explorer won’t have a parent in process tree.
Children 👧 : iexplore
Singleton ☝️: No
Path to file 🛣: %Systemroot%\
Account: Local Users
Start time: varies
iexplore
Parent 🤱: explorer
Children 👧 : None
Singleton ☝️: Yes
Path to file 🛣: Program Files\Internet Explorer\iexplore.exe
Account: Local Users
Start time: Boot
lsm
Parent 🤱: wininit
Children 👧 : None
Singleton ☝️: Yes
Path to file 🛣: System32
Account: Local System
Start time: Boot
services
Parent 🤱: wininit
Children 👧 : svchost, taskhost
Singleton ☝️: Yes
Path to file 🛣: System32
Account: Local System
Start time: Boot
Quick Check List
Singletons vs Cloners
Singletons: System, wininit, lsass.exe, lsm.exe, lsaiso, services.exe
Cloners: sms, taskhost, winlogon, iexplore, explorer, svchost, csrss
grep -E -i "(system|wininit|lsass|lsm|services)" "psscan.txt|pslist.txt" > singletons.txt
Boot vs Varies
Boot: System, sms, wininit, lsass, lsm, svchost*, services, csrss
Varies: taskhost, winlogon, iexplore, explorer, svchost*
grep -E -i "(system|wininit|lsass|lsm|services|sms|csrss)" "psscan.txt|pslist.txt" > boottime.txt
grep -E -i -v <2019-01-20> psscan.txt > nonboot.txt
System32 vs Other
System32: System, sms, wininit, taskhost, lsass, winlogon, lsm, svchost, services, csrss, lsaiso
Other: iexplore, explorer
WinCore vs Other
Non Wincore:
grep -E -i -v "(system|wininit|lsass|lsm|services|sms|taskhost|winlogon|iexplore|explorer|svchost|csrss)" "psscan.txt|pslist.txt" > all_non_core.txt
WinCore:
grep -E -i "(system|wininit|lsass|lsm|services|sms|taskhost|winlogon|iexplore|explorer|svchost|csrss)" "psscan.txt|pslist.txt" > all_non_core.txt
References
[1] SDF Podcast, by Michael Leclair


